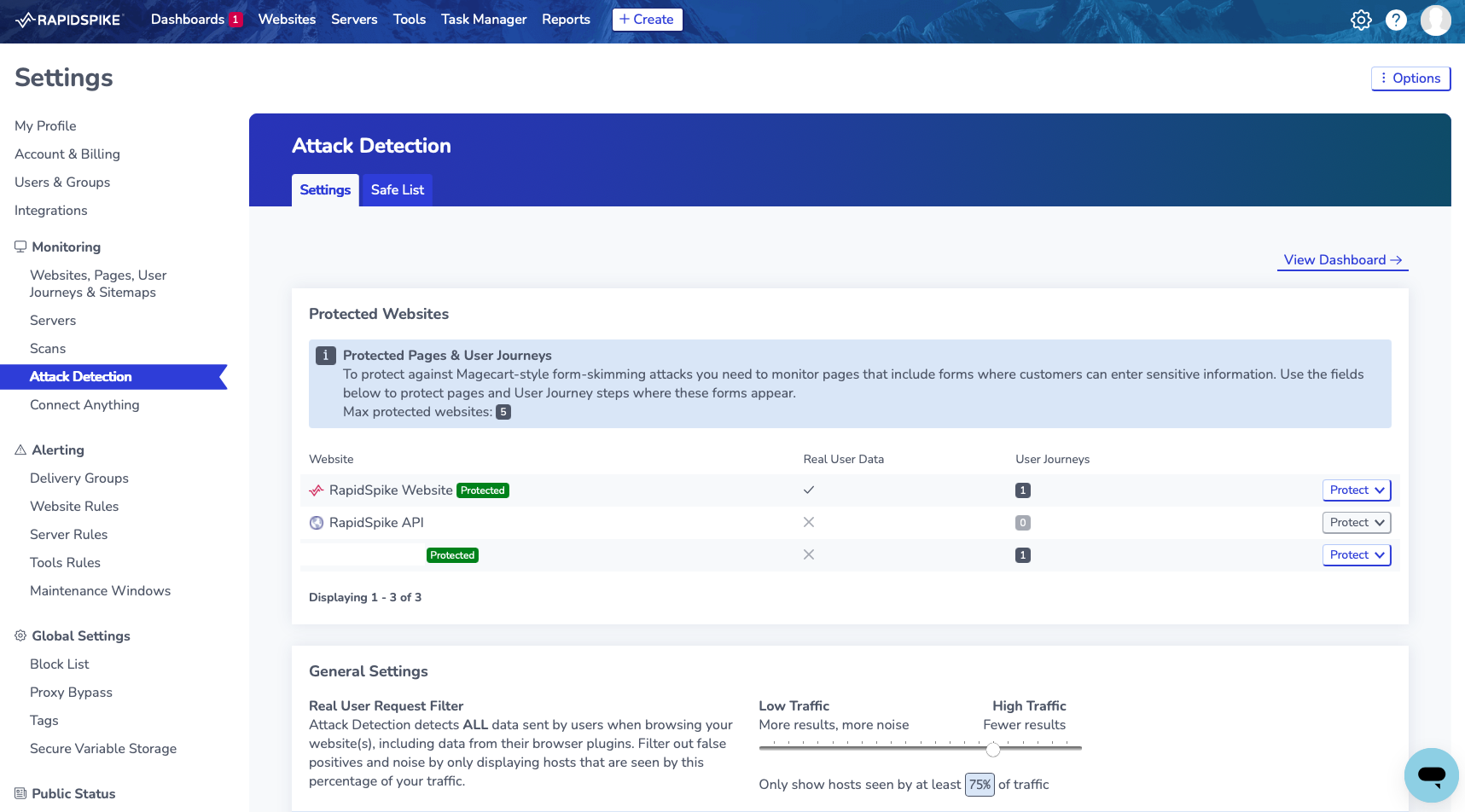
Using Real User Request Filter to Reduce False Positives
Use the Real User Request Filter to avoid false positives and noise in your RUM Attack Detection data. It does this by only displaying pending hosts that are only present in a percentage of page views. This helps you avoid alerts for hosts created by individual users’ browser extensions.
Attack Detection detects all data sent by the browser when users enter information on your website. For Attack Detection including Real User Monitoring, this includes data from browser plugins and extensions.
For example, a user might have a browser extension installed: each time they navigate a website, the extension injects code into the website. RapidSpike records these hosts with all other requests.
Edit the Real User Request Filter
Go to Settings > Attack Detection .
Use the Slider to adjust the percentage of page views where Real User Monitoring should observe a host before it shows up in your results. The higher the percentage, the fewer hosts you are likely to see; however, you will filter out more false positives.