Filters Fast knowingly allowed approximately 3.4 Million customers to shop on their compromised website for over 5 months, in a year-long data breach.
FiltersFast.com sells a variety of home filtration products. The company is based in North Carolina, USA, and according to SimilarWeb, the company averages approximately 574,190 website visitors each month.
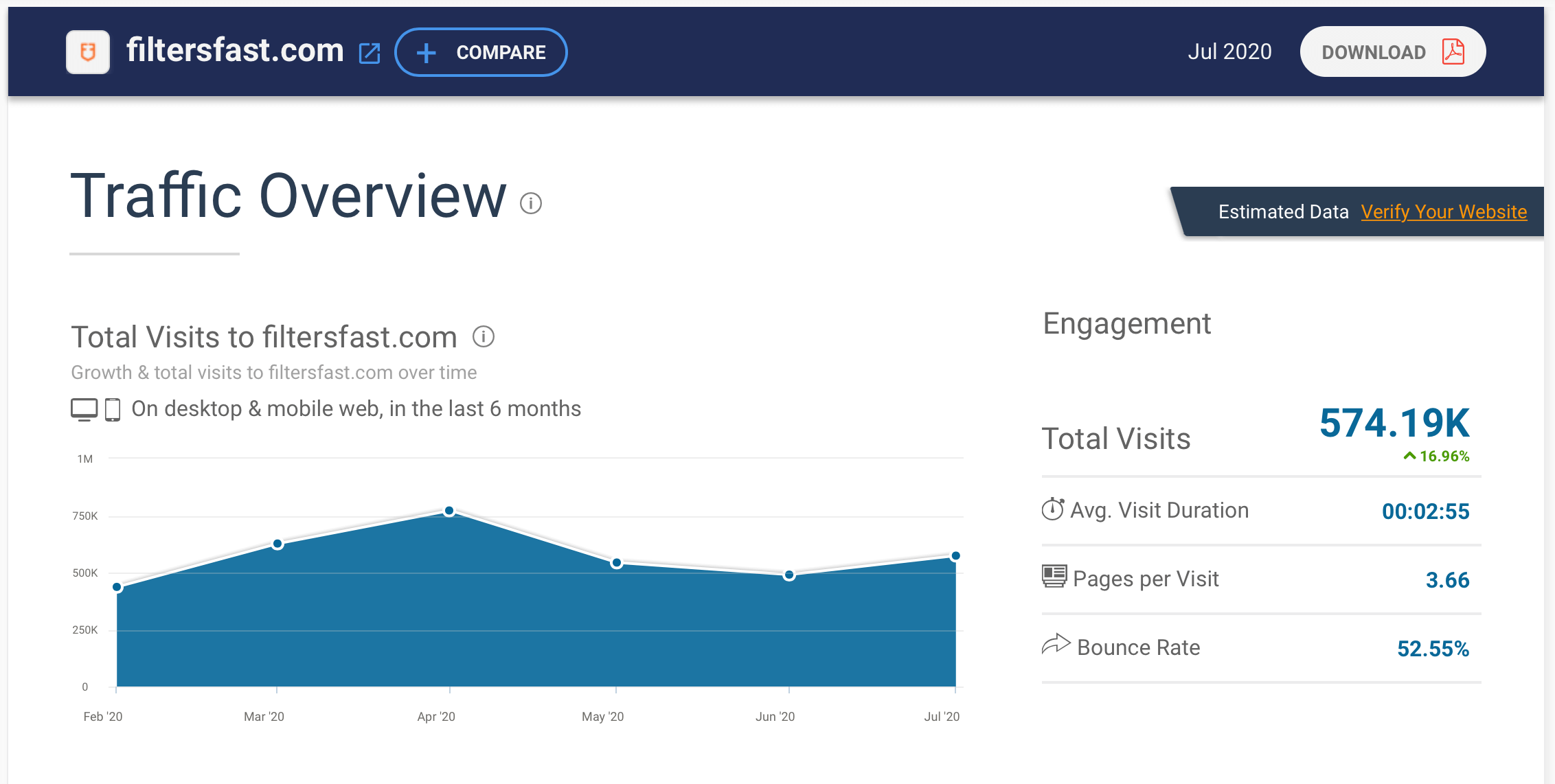
Notice of Data Breach
In a Notice of Data Breach sent to customers, the company explains that in late February 2020, “Filters Fast was made aware of a possible data security incident affecting its e-commerce website”. The company did not take their website offline to investigate, and therefore unaware customers were able to continue to shop on the compromised website.
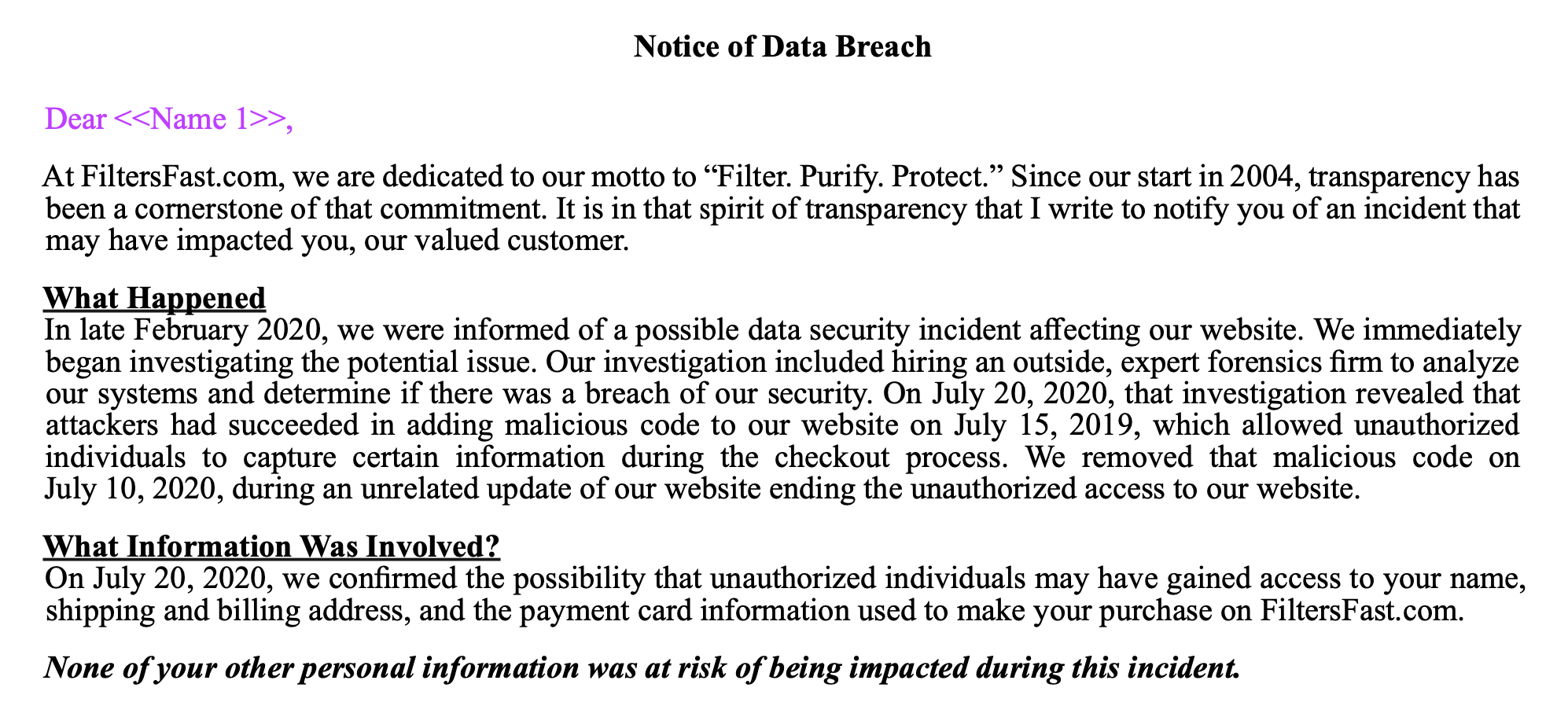
The company goes on to say that after an investigation, it was revealed on July 20th, 2020 “…that attackers had succeeded in adding malicious code to the Filtersfast website on July 15, 2019, which allowed unauthorized individuals to capture certain information during the checkout process.”
This means that any customer who purchased from the website between July 2019 and July 2020 most likely had their personal and credit card information stolen.
The code was removed from the website on July 10th, 2020, “during an unrelated update of the website, ending the unauthorized access”. Stolen information included name, shipping and billing address, and payment card information.
Filters Fast notified customers between 14th-18th August 2020, one month after discovering the malicious code and patching the vulnerability. The company states that it is unlikely that this event will result in identity theft, however, in reviews on Trustpilot made by customers, some have already noticed unauthorised purchases on their credit cards. The company is providing 12-months of identity theft protection services for affected customers.
It is unknown exactly how many customers this data breach has affected. In a series of notification letters to various Attorney Generals, Filters Fast states that they are notifying approximately 26,093 individuals who reside in California, 755 individuals in North Dakota, and 3,272 individuals in Iowa of the cyber attack. Therefore, there are at the very least 30,000 victims in this attack.
Filters Fast Customer Responses
Understandably, customers are not happy about the timeline of the data breach. Various users on Trustpilot and Twitter have expressed their disappointment in the lack of urgency from the company.
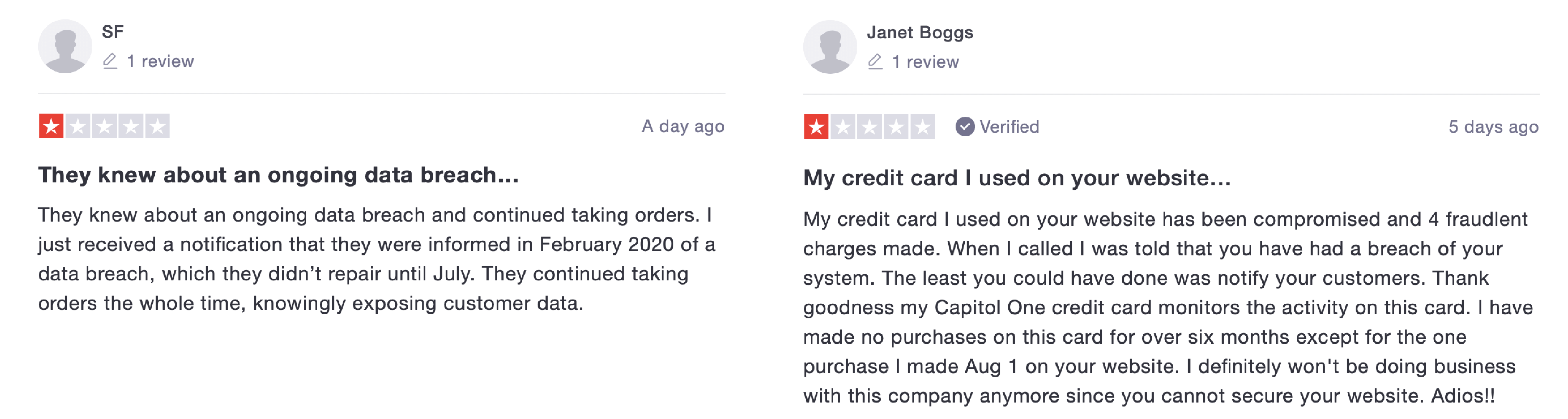
The company replied to tweets, in one stating; “With any event like this, it takes time to gather the relevant information, identify the affected individuals, hold the necessary internal discussions, and make the appropriate decisions to line up the assistance services that are being offered. Compounding this, the attacker’s activity was highly sophisticated, making the work of investigating the incident quite complex and time consuming. FiltersFast.com was also diligent with the investigation to ensure the appropriate protection services would be provided.”
RapidSpike’s Comments
RapidSpike Security Researcher comments on the attack; “This attack follows a similar modus operandi to other Magecart/web-skimming attacks seen in recent months and years. Although these can be sophisticated attacks, the company did not act appropriately in minimising data exposure. It is irresponsible for companies to knowingly allow their customers to shop on a website that is compromised.
“We recommend companies put their website into maintenance mode as soon as they are aware of a compromise. Then take time to locate the vulnerability and patch it, before allowing customers to shop on the site again.
“It is predicted by SimilarWeb that over 3.4 million customers shopped on the Filters Fast site from February – July 2020. This puts each of those visitors at risk of data theft had they made a purchase. Additionally, the company took a month to inform customers of the breach. Although it is important to take some time to ensure the information provided is accurate, this is not an appropriate timeframe for notification.
“Companies should take responsibility for protecting customers’ data by having a multi-layered approach to security, including continuous monitoring to prevent and detect attacks.”
RapidSpike security researchers have investigated the client-side security attack mentioned. We have also reached out to Filters Fast and have made ourselves available to help. We can confidently say our Attack Detection would have detected these types of attacks. Attack detection takes less than 5 minutes to set-up and will alert you to any untrusted data on your ecommerce site.






