Our sources state that there has been a 20% increase in web-skimming attacks since the outbreak of the COVID-19 virus. Recently, we have witnessed some high-profile Magecart attacks on websites which have gained popularity during the pandemic, including fitness-based websites. The latest fitness-based website attack reported is YogaFit, who were compromised for over 6 weeks.
YogaFit
YogaFit describe themselves as “the largest yoga school in North America”. Founded in 1994, the company has over 78,000 social followers.
Catalin Cimpanu from ZDNet first tweeted about the attack on July 17th:
In a Notice of Data Breach sent to affected customers, they state; “On or about May 27, 2020, YogaFit began investigating a report from a customer of an unusual payment card charge.” They go on to explain how they started an investigation to discover they were a victim of a “…sophisticated cyber-attack that may have resulted in a compromise to some of its customers’ credit and debit cards…”.
The attack took place between April 11th, 2020, and May 27th, 2020. Malicious code on the website may have stolen credit or debit card data from its website. Similar to other attacks, the information at risk includes the cardholder’s name, address, credit card number, expiration date, CVV, username and password.
YogaFit has now reassured customers that they have now taken the steps to secure the website and payment information will now be secure. They have reviewed existing policies and procedures, implemented additional safeguards and notified impacted individuals, as well as state regulators.
This is not the only high-profile fitness company to suffer an attack during the pandemic. In June we also reported an attack on ‘the largest speciality exercise equipment retailer in Canada’, Fitness Depot. The hack occurred from February 18th until May 22nd, during a 55% boost in fitness equipment sales.
Why has there been an increase in attacks?
Websites with products/services targeting popular at-home activities including homeware and gardening, cooking and kitchenware, online tutorials, and home-fitness, have all seen spikes in both website traffic and cybersecurity issues since the pandemic. Cybercriminal groups – including some Magecart groups – seek to attack popular websites as they may have a larger amount of data to steal and therefore higher ROI for the hackers.
Due to the pandemic many businesses have moved completely online, and companies are trying to cope with the influx of traffic. These sites are being changed and updated regularly which could lead to security vulnerabilities.
Bleeping Computer recently reported that the U.S. Federal Bureau of Investigation (FBI) has warned of an increased number of reports coming from victims of online shopping scams. Additionally, the Federal Trade Commission (FTC) explained that during April and May 2020, more reports of online shopping issues were received than in any other month on record.
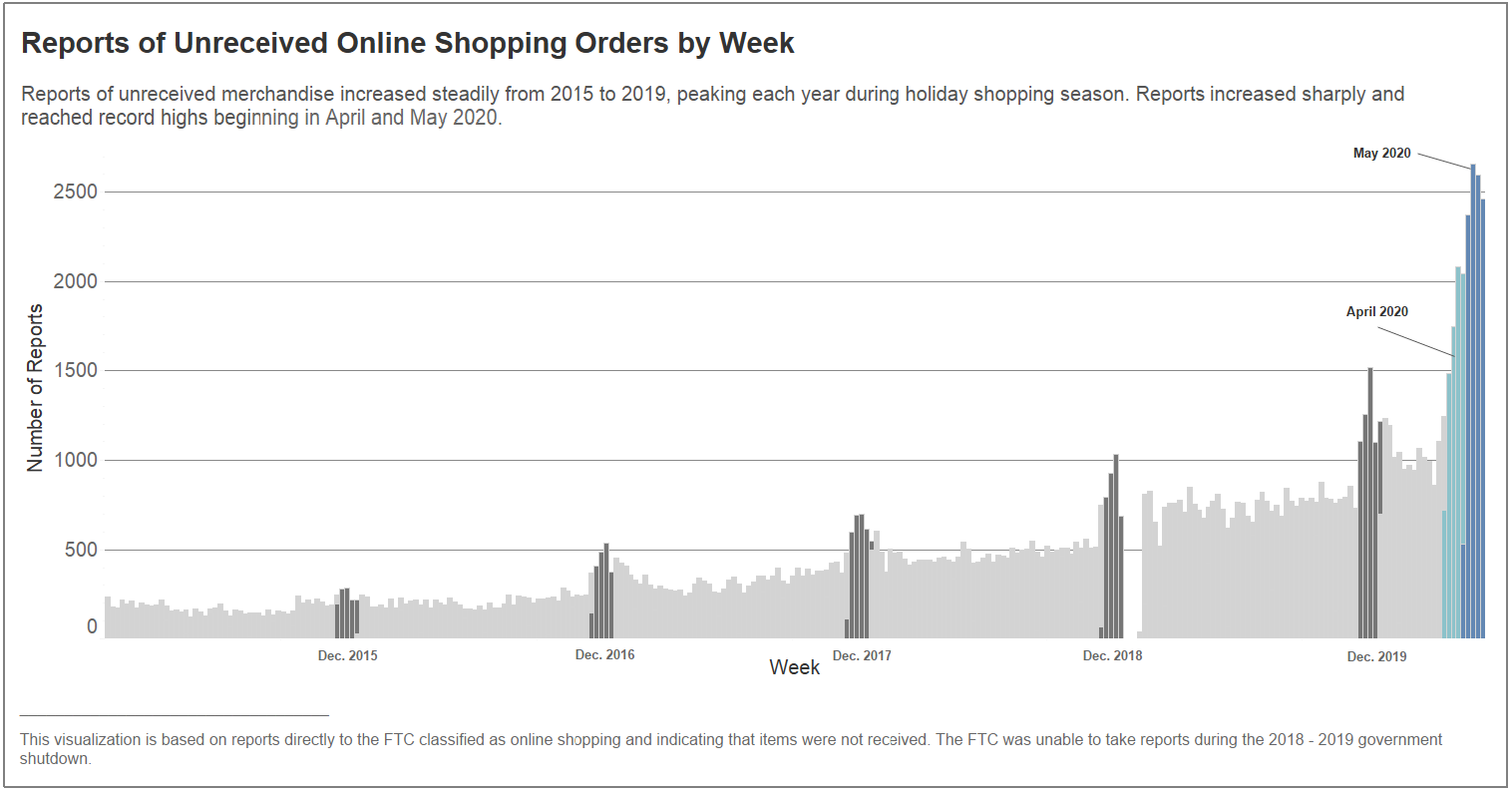
Companies need to take responsibility for protecting customers’ data by having a defence-in-depth approach to security. This is essential in the detection and prevention of cyberattacks. Consumers should be cautious whilst shopping online. The FBI state “Victims reported they were led to these websites via ads on social media platforms or while searching for specific items on online search engines’ “shopping” pages.” Consumers are also recommended to use a credit card where possible.
RapidSpike security researchers have taken the time to investigate the client-side security attack mentioned. We can confidently say our Attack Detection would have detected these types of attacks. Attack detection takes less than 5 minutes to set-up and will alert you to any untrusted data on your ecommerce site.






