Prevent and Detect Magecart Attacks
Rapid and accurate detection for Magecart breaches, website skimming, formjacking and supply chain attacks. Protect your customer’s data, prevent massive fines and avoid damage to your business’ reputation.
No install needed – discover data exposure in minutes.
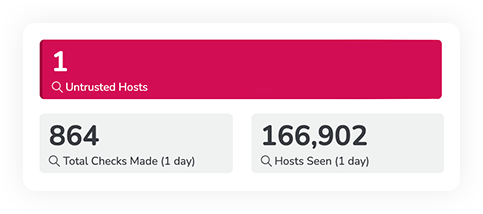
See how it works:
Defend against Website Data Breach Attacks
Do you know when your customers’ personal and financial data is being stolen from your website?
There are 4,800 formjacking attacks each month, with many reported in the press causing huge reputational damage to a business.
- RapidSpike protects brands of all sizes – from global multinationals, to small independants.
The affected websites range from small online stores to large multinationals. Often these breaches are via third party suppliers.
- RapidSpike monitors all traffic – including all your third parties.
The average total fine for a breach is $3.92 million. The longer it occurs, the more affected customers – the higher the fine.
- RapidSpike can detect breaches instantly
How Do These Attacks Happen?
Magecart-style attacks occur by exploiting a vulnerability on the web server. They then either inject malicious JavaScript code into an existing file or edit the HTML of the website to call a new third-party JavaScript file that includes malicious code.
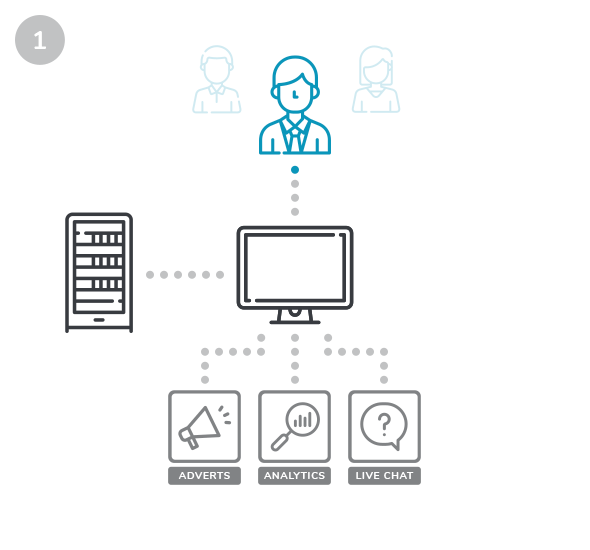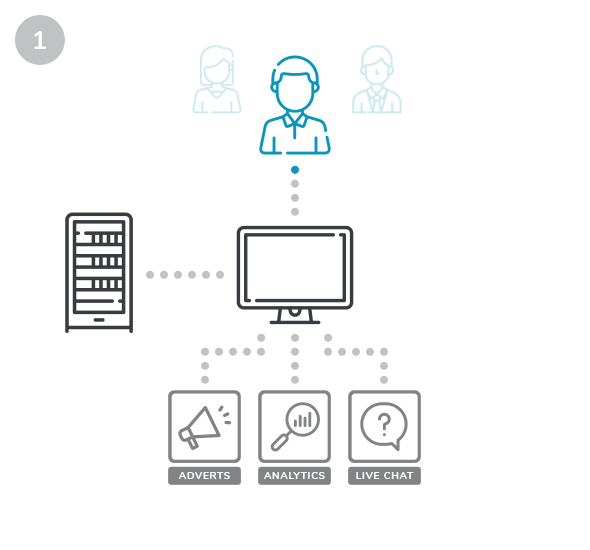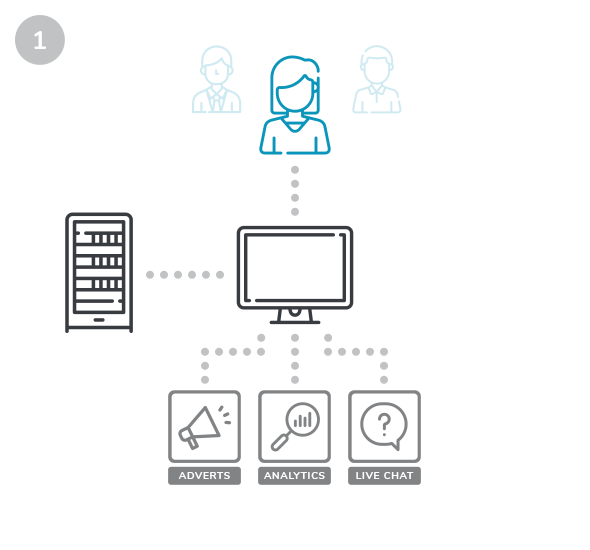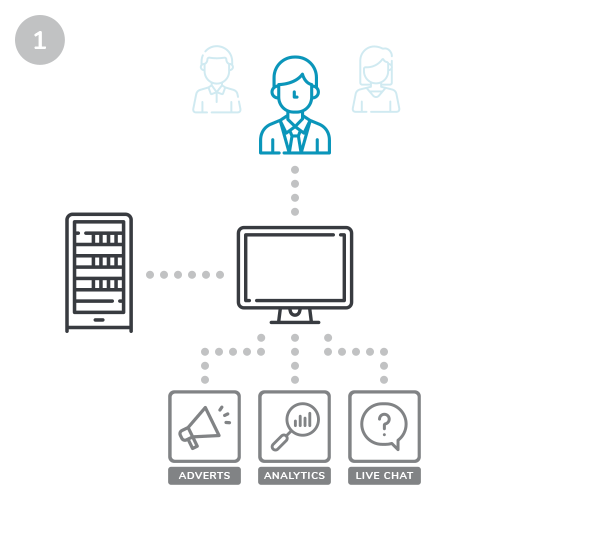
Whilst your customers browse and purchase on your website, scripts are loaded from third parties.
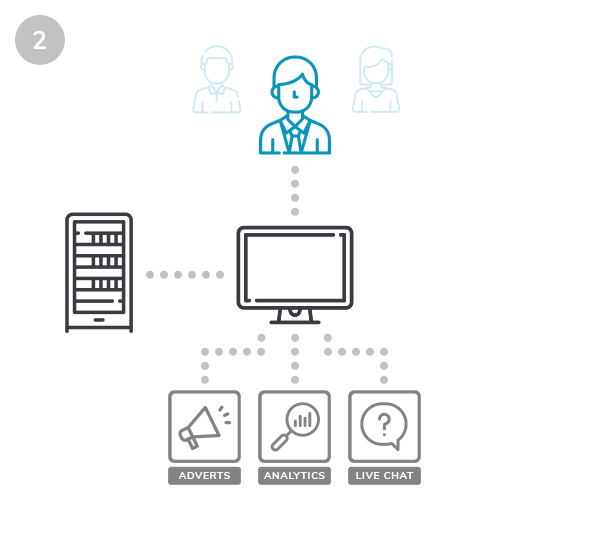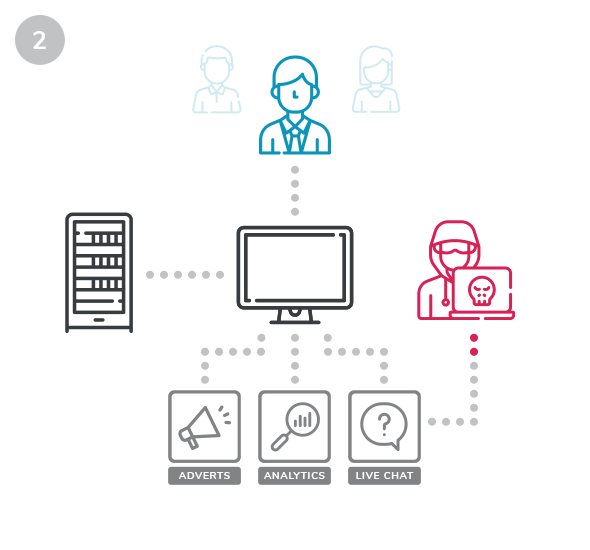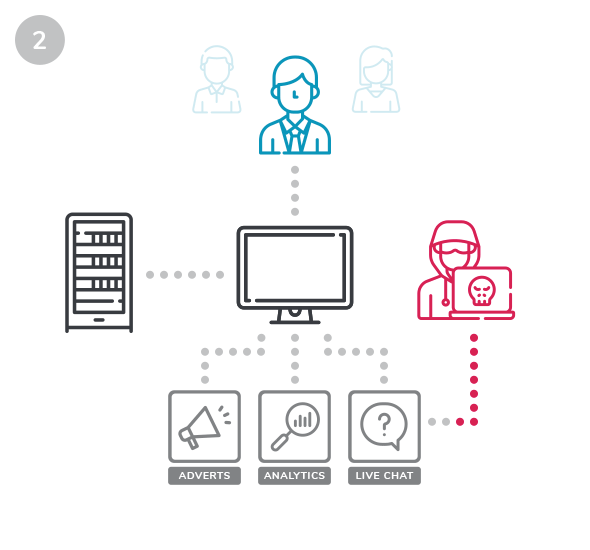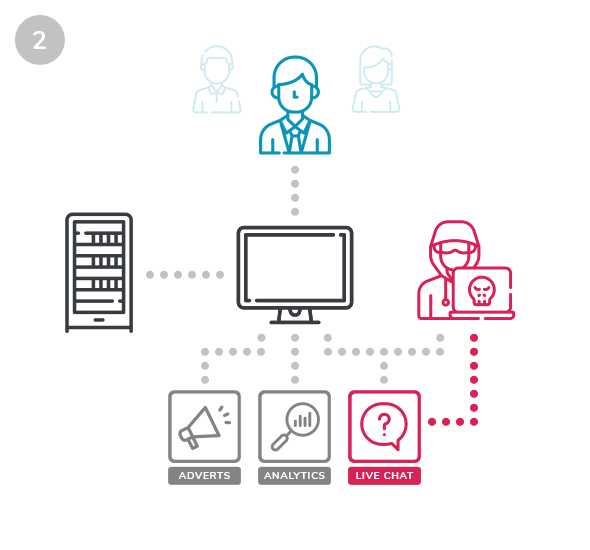
If a third party is compromised, hackers then have a way to write scripts affecting your website.
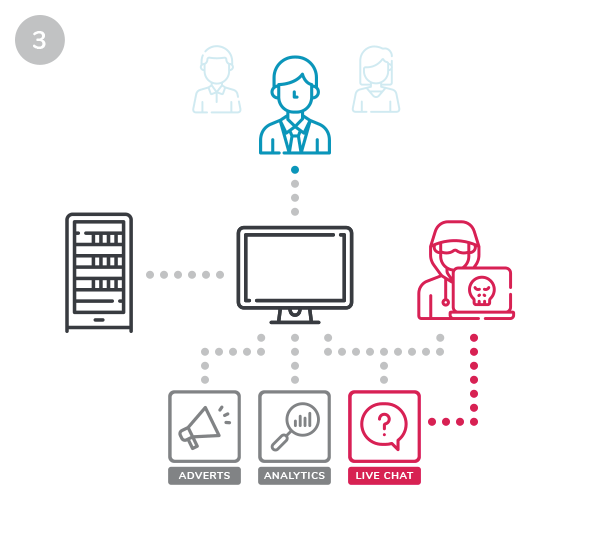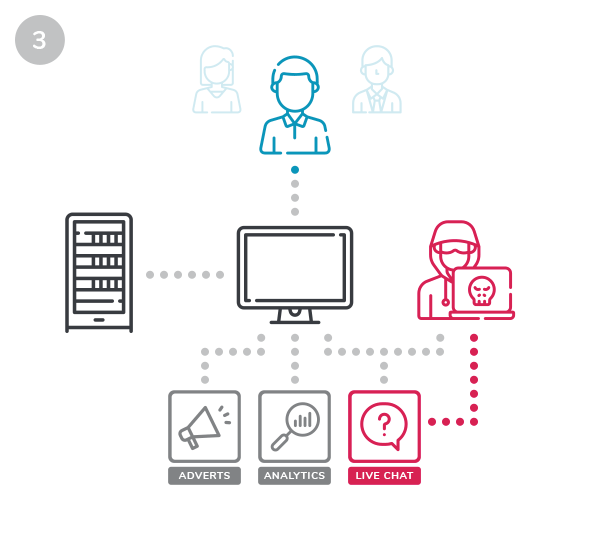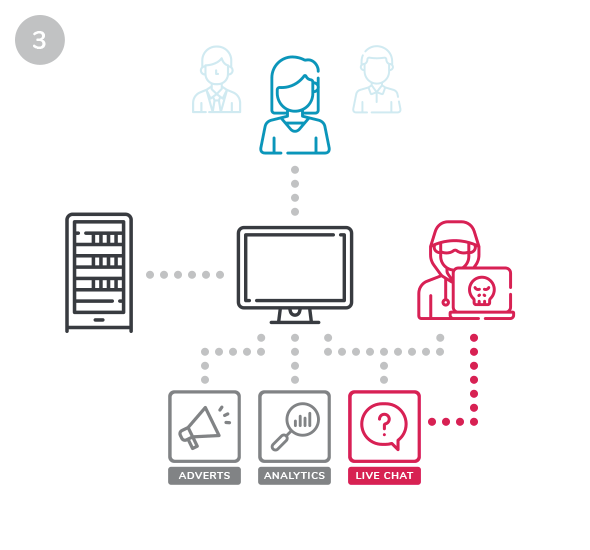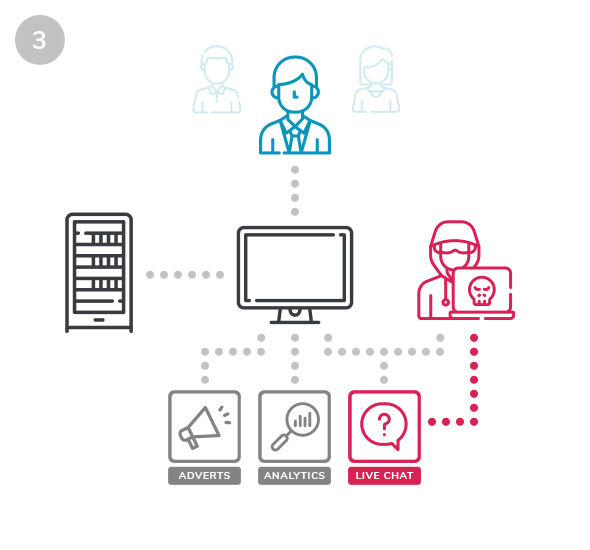
Hackers can then intercept customer card details without you even noticing, siphoning them off to an external server to see on the black market.
One Tool, Three Methods For Deeper Analysis and Protection
This multi-layered approach means we can examine more data points than ever before – helping us to understand exactly where customers’ information is being sent to, allowing companies to both proactively and reactively detect data breaches on the client-side faster than ever.
Synthetic Attack Detection
Continuously walks through the critical areas of your website, monitoring internal and third-party files – absolutely anything sending data from your website.
We build a whitelist of calls made from your website, and then warn you if any new destination hosts appear.
Real User Attack Detection
Monitor live traffic as it interacts with your website. We then collect information about where visitor data is being sent. If a malicious destination is added to your website, RapidSpike will alert you.
Magecart Attacks Are Affecting All Sizes of Business
Victims include major retailers, global leading brands, international and small independent businesses:

- 380,000 customers affected
- £20 million fine
- 16 days before detection
- Huge press coverage
Details were taken via a script designed to steal financial information by skimming the payment page before it was submitted.

- 40,000 customers affected
- 4 months before detection
Malicious software on third-party customer support product caused the hack. Stolen details included; names, addresses, email addresses, telephone numbers and payment details.

- 6,600 customers’ details stolen
- 5 days before detection
JavaScript file was injected into the Vision Direct website posing to be a legitimate Google Plugin. Vision Direct have provided all affected customers with an Identity Monitoring Service.

- 20 million US citizens affected
- Website hacked for 8 months
- $3.8m spent on mailing notices
AMCA have filed for Chapter 11 protection and listed assets of $10 million. Multiple lawsuits against AMCA and the companies this breach affected have been filed.

- 6,589 websites affected
- 239,000 payment details sold for $1.6million
- Infected for 26 days before detection
Volusion are an ecommerce shopping cart provider. The malicious file and domain were both disguised to look legitimate.

- 1 week before detection
The breach occurred from October 7th – 15th, 2019. An unauthorised third-party added malicious code to two pages on macys.com, including the checkout page and the wallet page.
The Benefits of Magecart Attack Detection
RapidSpike Magecart Attack Detection can secure your website with the following benefits:

Reduce Detection Time
Reduce the detection time from 12 days to under 5 minutes

100% Awareness
Ensure no malicious destinations get added to your website without your prior knowledge

No Unauthorised Changes
Easily and continuously protect against unauthorised changes to your critical JavaScript files

Detect All Magecart Attacks
Detects website skimming, form-jacking and supply chain attacks.

Comply With Legislation
Clear evidence for the ICO that you have taken steps to defend yourself

Monitor Your Supply Chain
You can’t secure what you don’t own – assure your third-party supply chain

Real Time Monitoring
Continuously monitor for changes before, during and after the event

Up-To-Date Protection
Research and Development into new threats on a weekly basis

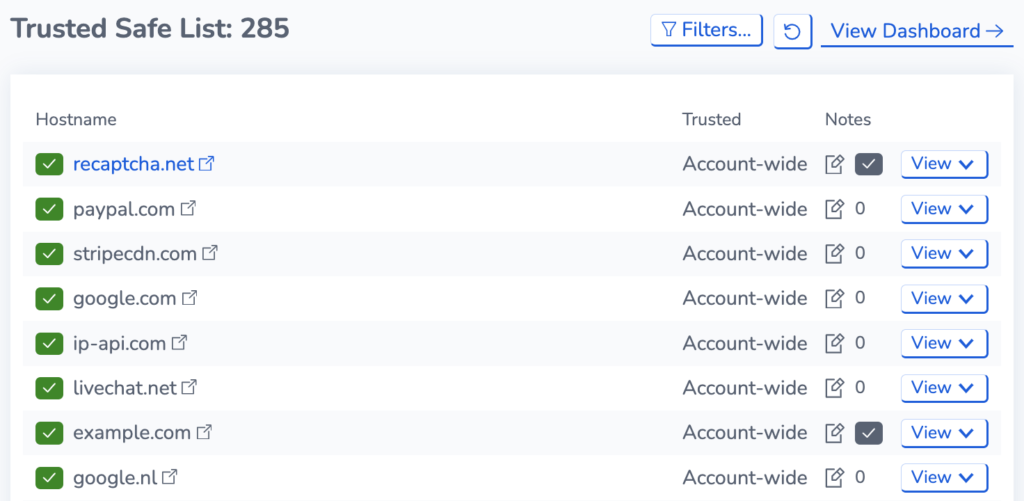
Access our Global Security List
Comprehensive trusted and untrusted domains database to help you decide quickly who to trust

Comprehensive Alerting
Receive alerts of any issues in the format of your choice (Email, SMS, Voice, Slack and more)

Avoid complex CSPs
No need to lock down everything with overbearing content security policies
