RapidSpike would like to make a statement about how one of our developers assisted the City of York Council with a potential data breach on their One Planet York mobile app in early November.
TL;DR: Our Summary
Our developer identified a significant security vulnerability with the One Planet York app: it was sending the personal details of its users, to other users of the app, whenever the ‘Leaderboard’ page was selected.
Despite the framing of this vulnerability report by the City of York Council, this vulnerability was disclosed following the Council’s own responsible disclosure guidelines. Our developer initially emailed the ‘oneplanetyork@york.gov.uk’ address, whose agent promptly forwarded his report to the Council’s ICT Security Team:
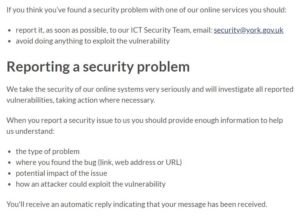
It is important to note here that our developer did not do ‘anything to exploit the vulnerability.’ He simply browsed to a page within the app, as any user would.
We’re releasing this statement in response to the reporting of the data breach and to help protect and encourage white hat security researchers who perform an absolutely critical role in the fight against cybercrime.
So, What Happened?
We’ve recently been developing new security features for our Digital Experience Monitoring platform. Whilst building these features, our developer was utilising a number of diagnostic tools, including the popular Burp application. Whilst this tool was running, our developer noticed a number of unusual transactions between the One Planet York app and the API that powers it.
Accessing the app ‘Leaderboard’ screen caused the API to push the app’s top-ten users’ personal data, in plain text, to the app. This personal data included the users’ name, email address, phone number, postal address, postcode and other sensitive information such as their hashed password (which appeared to be a SHA256 hash, at least) and that password’s salt:

Whilst our developer saw the password salt stored and transmitted alongside the hash, at no time were Council servers compromised or otherwise accessed using this data. The data was sent in a GET from the ‘https://opyapp.appyork.com/api/user/leadership.php’ API endpoint. Hashed passwords and their corresponding salts are frequently used by attackers in similar situations to breach information systems. Fortunately, our developer found this fundamental security weakness before it could be exploited by an attacker.
We must be really clear at this point: our developer did not manipulate any requests. The app simply transmitted this personal data as a response to the GET request for the ‘Leaderboard’ page. This personal data was sent to any user of the app when they browsed that page.
Although the personal details of only a very small number of users were observed in these API calls, we do not know if manipulating the API calls could have exposed more. Our developer did not attempt this, or any further action. Instead, he immediately, after seeking advice, informed the City of York Council data protection and security officer. In subsequent email exchanges, he responded in a timely manner to further requests for information, stating clearly that he stumbled across a security vulnerability, that he was informing the council in good faith, and that they did not store any of the personal data that had been exposed by the app.
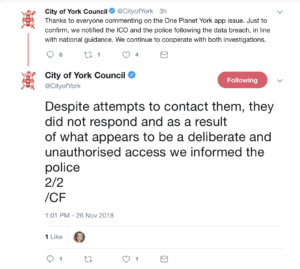
York City Council subsequently released details of the responsible vulnerability disclosure but instead chose to call it a ‘deliberate and unauthorised access by a third party,’ before reporting our developer to the police. The Council justified this by saying they were unable to contact him:
Our developer actually replied to their email in just 18 minutes of their initial email:
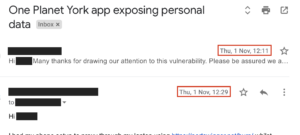
He then replied to their subsequent email, asking for our developer to delete any personal data, within the same working day:
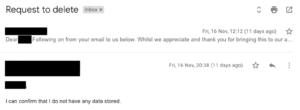
The Council’s initial statement and subsequent public media reporting left us confused with the portrayal of the issue. There is an established precedent in the UK for legitimate security researchers to disclose vulnerabilities within information systems to relevant security teams. The Council’s positioning of this good-faith disclosure as a deliberate attack flies in the face of the UK Government’s National Cyber Security Centre advice on the matter, and the International Standard framework for vulnerability disclosure.
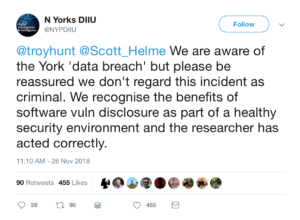
We have to say that North Yorkshire Police’s Digital Investigation & Intelligence Unit dealt with the whole situation superbly, and should be commended for their approach. It must also be noted that the security community have also stood up and supported our developer, even without the full story.
People who detect security vulnerabilities should be encouraged to responsibly disclose their findings to ensure that issues are resolved swiftly, and North Yorkshire Police agree:
Timeline of Events
- 26 October 2018 – Security vulnerability discovered by the developer.
- 27 October 2018 – Developer sought advice from a known security expert about responsibly disclosing the security bug.
- 27 October 2018 – Developer contacted the One Planet York team, informing them they were exposing personal data and expressed concern that a malicious person could exploit the vulnerability.
- 31 October 2018 – Developer received a confirmation email from One Planet York that they had received the email and had forwarded it onto their IT team.
- 1 November 2018 – Developer received an email from the City of York ICT Digital Manager asking for more information about how the vulnerability was discovered.
- 1 November 2018 – Developer replied giving full details of how it happened, the method and tool that was used, details of the API endpoint exposing personal data and that he just wanted to let them know about it, but was not intentionally seeking issues (the API was freely disclosing the data).
- 16 November 2018 – York Information Governance & Feedback Team emailed our developer asking him to delete the data else he would be “subject to obligations as a data controller, under the General Data Protection Regulation (GDPR) and Data Protection Act (DPA) 2018”.
- 16 November 2018 – Developer replies to confirm he does not have any data stored. No data was ever actually stored on disk as it was just observed in the response from the API after he loaded a page within the app.
- 18 November 2018 – City of York Council issue a letter regarding the vulnerability and emailed all users of the One Planet York app to inform them that they have “notified the police of this deliberate and unauthorised access by a third party”.
- 19 November 2018 – York Press publish details of a “hack” – Nearly 6,000 people hit by data breach after York council app hacked.
- 20 November 2018 – BBC and Telegraph plus numerous technology and security blogs report on the “hacker” and “mysterious third-party”.
- 26 November 2018 – Troy Hunt tweets that the Council’s breach notice does not “feel good”. Scott Helme retweets Troy’s tweet and echos his concerns.
- 26 November 2018 – North Yorkshire Police’s Digital Investigation & Intelligence Unit are quick to tweet that they are aware of the data breach and “don’t regard this incident as criminal”.
- 26 November 2018 – City of York Council tweet they “tried to contact” our developer and that he “did not respond”.
- 26 November 2018 – North Yorkshire Police Cyber Crime Unit call our office to speak to our developer, but unfortunately he isn’t in the office.
- 26 November 2018 – North Yorkshire Police Cyber Crime Unit emails our developer to tell him the “council have reported the matter as a Computer Misuse Act offence” but the police are “not treating the matter as such based on the information provided”.
- 27 November 2018 – RapidSpike make a public statement on the matter, after seeing what had been reported in relation to this vulnerability disclosure.
We support our developer’s actions, and believe he acted in the public’s best interests at all times. The handling of the One Planet York data breach led the public, our developer and our team to have some anxious moments until the police confirmed all was OK.
At RapidSpike we are trying (amongst other things) to help the world combat cybercrime. A relative of one of our own team was hit by the recent Vision Direct breach. This and the One Planet York vulnerability brings home the need for us to become even more focused on the ongoing fight against online fraud.
About RapidSpike
RapidSpike is a Digital Experience Monitoring Platform that interacts with digital platforms exactly as customers do.
Fast, secure and well structured digital platforms achieve better revenue conversion, improve user experiences and reduce global energy consumption.
RapidSpike pinpoints critical platform issues and improvements by collating real time and synthetic data on customer interactions, system performance, and security into clear compelling actionable insights.
RapidSpike is a part of the Storm Technology Group that also includes the PCI QSA company Data Protection People, the malware protection company InfoSecurity People and the penetration testing company, Pentest People who have all supported us in the creation of this statement.
For more information visit: