Visa have reported a new security alert for an advanced, self-cleaning, JavaScript skimmer named Pipka. The security researchers at Visa’s Payment Fraud Disruptions (PFD) discovered the skimmer in September earlier this year. The skimmer was first seen on a North American ecommerce website which had previously been infected with a different skimmer, Inter. Visa have now identified another 16 additional sites with hosting the Pipka code.
Much like other website skimmers, the code targets payment data entered into payment forms on ecommerce websites. The malicious code will look for and extract payment data including: name, address, account number, expiration dates and CVV.
However, the Pipka skimmer has an advanced tactic to avoid detection. Visa’s PFD team describes this in their report; “The most interesting and unique aspect of Pipka is its ability to remove itself from the HTML code after it is successfully executed. This enables Pipka to avoid detection, as it is not present within the HTML code after initial execution.”
This self-cleaning tactic makes the code less likely to be detected to website owners. RapidSpike Security Researcher explains the process: “The Pipka skimmer is very clever, it makes it very difficult to detect. Normally you would load a website, then view the source and the malicious code would be there. However, with Pipka, as soon as the website loads, the malicious code is removed. Therefore you could never see it if you looked for it in the usual way.”
Understanding the code
Upon finding a vulnerable website, Pipka is injected into the checkout form code, ready to steal any data entered into the form. The data is base64 encoded and encrypted using ROT13 cipher and checks for duplicate data. Once the checks are carried out and if the string is unique, the data is exfiltrated to an external server. Once the skimmer executes, it calls the ‘Start’ function which looks for data every second and then calls the ‘Clear’ function which locates the skimmer script tag and removes it, essentially, cleaning up itself!
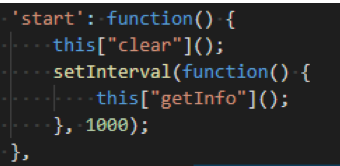
Full details of the code can be found in the report.
The Visa PFD team explains; “This is a feature that has not been previously seen in the wild, and marks a significant development in JavaScript skimming.”
Recommendations
This new skimmer means more advanced detection is required to avoid prolonged infection time. Visa give some recommendations in their report, firstly; “Institute recurring checks in eCommerce environments for communications with the C2s provided in this report.” Communications with the C2’s (C2s stands for ‘Command and Control’) means checking the servers the data is sent to. Luckily, RapidSpike Magecart Detection does exactly this! We alert you if we detect data being sent to any untrusted hosts from your website. This reduces detection time from weeks to minutes.
RapidSpike Vulnerability Scanner will also continuously monitor your digital ecosystem for security vulnerabilities, helping to avoid the opportunity for website skimmers to take advantage of your site in the first place.
If you are concerned about the security of your ecommerce site, RapidSpike can put your mind at ease. Get in touch today and our helpful team can explain how you can take back control of the security of your site.






