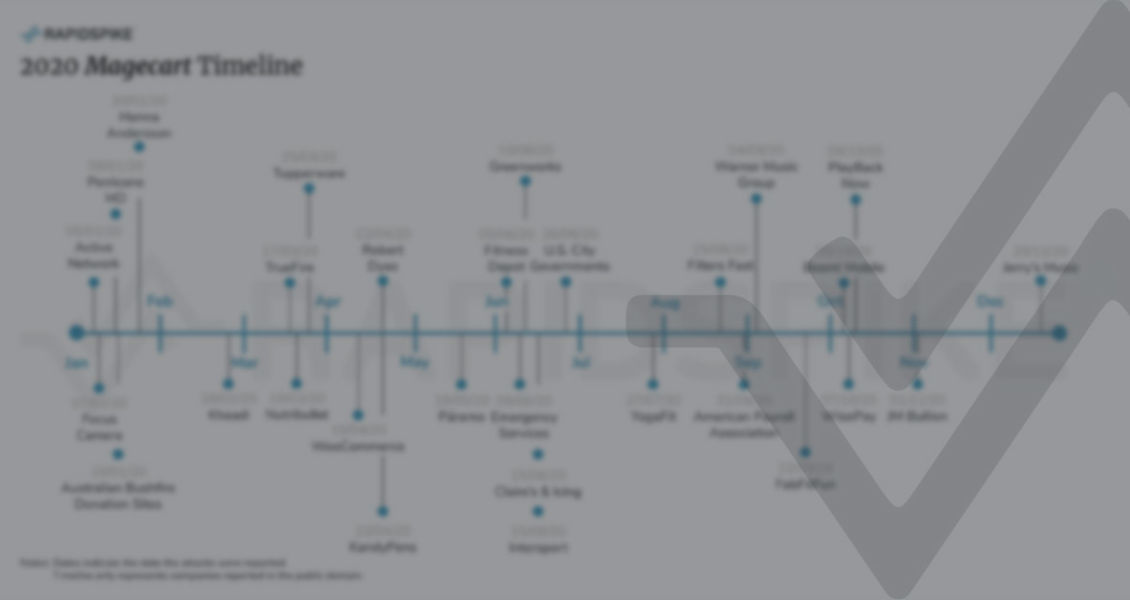
In this blog, we break down the timeline of the number one hacker threat to ecommerce sites today – Magecart. The 2020 Magecart timeline includes all the significant Magecart attacks in 2020. With 4,800 formjacking attacks each month alone, this timeline only represents a small proportion of attacks reported in the public domain in 2020.
2020 may have been a slow & tough year for some, but the hackers haven’t stopped, in fact given the rise in ecommerce transitions due to Covid-19, there has been an increase in both attack numbers and sophistication.
You can detect Web-skimming, Formjacking, and Supply Chain attacks before a data breach occurs with RapidSpike Magecart Attack Detection.

Active Network
The first reported Magecart attack of 2020 was an attack on school management software provider Active Network. ZDNet revealed hackers had gained access to Blue Bear, a school management platform that handles school accounting and online stores. Parents who paid school fees or bought via online stores had their credit card details stolen. The attack was active over 6 weeks from October 1st, 2019, and November 13th, 2019.
Focus Camera
On January 7th, Bleeping Computer reported an attack on photography retailer Focus Camera. The specific attack dates are unknown however customers who shopped on the site from late December 2019 until January 2020 may have had their personal and financial details stolen.
The malicious domain (zdsassets.com) was registered on November 11th, 2019 in the Netherlands. The domain is difficult to spot in comparison to the legitimate ZenDesk domain (zdassets.com). The attacker modified a JavaScript file to inject an obfuscated payload, encoded using base64. As of January 6th, the malicious code is no longer active on the site.

Perricone MD
In a blog post, a RapidSpike Security Researcher explains how we discovered multiple attacks on science-based skincare brand, Perricone MD. The attack affected perriconemd.co.uk, perriconemd.it and perriconemd.de. The two hacking groups involved were able to insert malicious code directly into the websites. The first hack can be traced back to November 2018, the second hacking group gained access to the websites a year later in November 2019, likely through the same vulnerability. They registered an imitating domain, perriconemd.me.uk to go undetected and only loaded the skimmer on the checkout page.
Despite numerous attempts being made to contact the company, no one acknowledged the attack on the site. The code was finally removed on 11th January.
Australian Bushfire Donation Sites
On January 10th, it was revealed that sites raising donations for the Australian bushfires had been compromised. Bleeping Computer explains; “When a visitor of the site adds an item to their cart, such as a donation, a malicious credit-card skimmer script named ATMZOW will be loaded into the checkout pages. When a user submits their payment information as part of the checkout process, the malicious script will steal the submitted information and send it to the vamberlo[.]com domain. This domain is obfuscated in the script.” Security Researcher Troy Mursch used the PublicWWW tool and discovered this same script was active on 39 other websites.

Hanna Andersson
On January 20th, Bleeping Computer revealed that the popular US children’s apparel retailer Hanna Andersson had disclosed an attack on their website. The website was hacked and malicious code was injected to steal payment details from the checkout pages. In an email to customers on January 15th, Hanna Anderson stated: “On December 5th, 2019, law enforcement informed Hanna Andersson that credit cards used on its website were available for purchase on a dark web site.” It was confirmed that the compromised date could be as early as September 15th, 2019.
Khaadi
During research into client-side attacks, RapidSpike observed a skimmer loading on the popular Pakistani fashion website, Khaadi. On January 23rd, RapidSpike’s Security Team discovered a skimmer on uae.khaadi.com and uk.khaadi.com which was active for over five weeks. The malicious code was injected into the source of the website and only loaded the skimmer on the /checkout/ page to help avoid detection. Once a customer is on the checkout page the malicious code loads a heavily obfuscated JavaScript file from hotjar[.]us. This domain was registered on 21 January 2020, just two days before the hack appeared on Khaadi. Once a customer has entered their card details on the checkout page and they have hit the “Place Order” button, all card details – including the three-digit CVC / CVV – are encoded and sent to the same malicious host.

NutriBullet
On March 18th, TechCrunch reported that popular blender company NutriBullet suffered a Magecart Attack on their website ‘nutribullet.com’. The code was present for 26 days from February 20th, 2020 until March 17th when NutriBullet removed the code. The code was specifically targeting the checkout page to steal payment information. It is believed to be Magecart Group 8 who have carried out the attack.
TrueFire
TrueFire is an online guitar tutoring platform with over 1 million users. They announced a data breach on their website in which an attack exposed customers’ payment information. The Hacker News reported the attack on March 17th, 2020. Affected customers posted the Notice of Data Breach letter they received from TrueFire online. The letter confirms the website was compromised for over 5 months from August 3rd, 2019 – January 14, 2020. The company confirmed they patched the web vulnerability that allowed attackers to compromise the website in the first place.

Tupperware
SC Magazine reported the attack on March 25th whilst the attack was still active. The attack, discovered on March 20th, occurred on the tupperware[.]com site and some local sites. Researchers discovered a suspicious iframe loaded from deskofhelp[.]com when visiting Tupperware’s checkout page, which displays the payment form fields used by shoppers. The domain was registered on March 9th and links to a Russian email address provider. Although the number of affected customers is unknown, the malicious code was present on the website for at least 6 days. On March 27th, Tupperware released a statement stating they “promptly launched an investigation, took steps to remove the unauthorized code, and a leading data security forensics firm was engaged to assist in the investigation.”
WooCommerce
On April 10th, ThreatPost reported that ecommerce sites powered by open-source plugin WooCommerce had been infected by web-skimming malware. It is unknown how exactly the attackers got into the site however, it is speculated that it was through exploiting a software vulnerability in WordPress or WooCommerce. The infection saves credit card information in plain text in the form of cookies. It then uses the legitimate ‘file_put_contents’ function to collect them into two separate image files which are saved in the ‘wp-content/uploads’ directory. As well as using several layers of encoding and concatenation to avoid detection, it also appears that the skimmer had self-cleaning abilities alike to the Pipka skimmer.

Robert Dyas
UK hardware site Robert Dyas suffered a web-skimming attack lasting over three weeks from 7th-30th March. In a Cyber Security post, the company explains; “We continue to investigate, as a matter of urgency, the theft of customer data between 7th March 2020 and 30th March 2020 from robertdyas.co.uk. The stolen data included personal and financial details of some customers during that period. This matter has been reported to the relevant authorities.” Robert Dyas have taken steps to close the vulnerability and are now “…continually monitoring the site and running security scans”. A spokesperson for Robert Dyas told The Register “We are in touch with approximately 20,000 affected customers and are recommending they also contact their bank or card provider and follow their recommendations as a precaution.”
KandyPens
On April 22nd, Technadu reported an attack on vaping pen and accessory site KandyPens. They explained that the company informed the California State General Attorney Office of a data breach. The company discovered a skimmer on the checkout page in January 2020. The skimmer was active on the site for 11 months from March 7th, 2019 until February 13th, 2020. Information stolen included; name, card number, expiration date, and (CVV). KandyPens explains in their Notice of Data Security Incident that they have now fixed the vulnerability and have increased website monitoring on their payment system.

Páramo
On May 19th, The Register reported the attack on the British outdoor clothing retailer Páramo. The attack lasted for almost 8 months from July 2019 and March 2020. In that time frame, 3,743 customers had their payment details stolen. Although the company had security scans set up, they failed to detect the malicious code. Páramo’s IT Director, Jason Martin explains how the hack took place, stating; “the hackers’ method used a PHP file which modified out IFRAME src so that it still loaded the PayPal code, but also loaded an external JavaScript file”. The malicious JavaScript code was named gcore.js and was hosted on a third-party URL. The company has now removed the hack, patched the vulnerability, and have Attack Detection tools to proactively monitor for other client-side attacks in the future.

Fitness Depot
Bleeping Computer reported the attack which affected the ‘largest speciality exercise equipment retailer in Canada’ – Fitness Depot. The hack occurred from February 18th until May 22nd, during a 55% boost in fitness equipment sales. From February 18th- April 27th, only customers with home delivery were affected, then from April 28th – May 22nd, any customers that ordered online were affected. In a Notice of Data Breach sent to affected customers, Fitness Depot explained; “Based on our preliminary findings it appears our Internet Service Provider [ISP] neglected to activate the anti-virus software on our account.” RapidSpike’s Security Researcher comments: “This is a great example of how companies need to apply a multi-layered security approach. It is not the responsibility of an ISP to protect a website against web-skimming attacks.
On June 9th, The Hacker News reported about attack groups leveraging misconfigured AWS S3 data storage buckets to insert malicious JavaScript into websites. Three compromised websites belonging to Endeavor Business Media were hosting code designed to steal payment information. The affected websites host emergency services-related content for firefighters, police officers, and security professionals. The attack affected: www[.]officer[.]com, www[.]firehouse[.]com and www[.]securityinfowatch[.]com.

Greenworks
RapidSpike’s Security Team observed a highly-sophisticated self-cleaning and self-destructing skimmer on the popular hardware tool website Greenworks. The hack was first spotted by RapidSpike’s Client-Side Security Scanner on June 8th. The hack came at a bad time amid a homeware and gardening boom. Greenworks’ website visitors statistics have reflected these increases. SimilarWeb estimated a 667% increase in Greenworks website visitors’ from 45,000 in February 2020 to 350,000 in May 2020. RapidSpike reached out to Greenworks and made ourselves available. The Greenworks team never replied to any members of our team, however, on June 12th the Greenworks website was put into maintenance mode. Full details of the attack can be found here.

Claire’s and Icing
On June 15th, it was revealed that accessories giant Claire’s and their sister site Icing had been infected with malicious skimming code for over 6 weeks. Willem de Groot discovered the attack on the sites back in April a day after all brick and mortar stores were shut down due to the COVID-19 pandemic. De Groot explains how the threat actors created a domain named ‘claires-assets.com.’ which laid dormant for four weeks until April 25th when a malicious script was added to the Claire’s and Icing websites. The malicious script was attempting to steal customers’ payment details from at least April 30th-June 13th.

Intersport
Reported the same day as the Claire’s and Icing data breaches, Intersport were also named as a victim of a web-skimming attack. Antivirus maker ESET revealed the attack on their Twitter. They explain how the skimmer affected regional Intersport websites in Croatia, Serbia, Slovenia, Montenegro, and Bosnia and Herzegovina. De Groot also researched the Intersport attack and discovered the company’s stores got hacked on April 30, cleaned on May 3, and then hacked again on May 14. ESET said the company removed the malicious code within hours after being notified of the latest hack.
U.S. City Governments
On June 26th, it was reported that eight U.S. city governments had web-skimming malware on their Click2Gov online payment platforms. This was a personalised attack as the skimmer is designed to only work with Click2Gov. When a customer made a payment on the platform, the skimmer sent the information to a remote server in the control of the hackers. Information stolen included: names, addresses, and credit card information. It was not revealed which cities this affected or how many customers had their data exposed. The attack was active from April 10th until after July 1st, 2020.
YogaFit
On July 27th, Catalin Cimpanu from ZDNet first tweeted about the attack YogaFit via Twitter. In a Notice of Data Breach sent to affected customers, they state; “On or about May 27, 2020, YogaFit began investigating a report from a customer of an unusual payment card charge.” They go on to explain how they started an investigation to discover they were a victim of a “…sophisticated cyber-attack that may have resulted in a compromise to some of its customers’ credit and debit cards…”. The attack took place between April 11th, 2020, and May 27th, 2020. Information at risk includes the cardholder’s name, address, credit card number, expiration date, CVV, username, and password.

Filters Fast
In a Notice of Data Breach sent to customers, the company explained that in late February 2020, “Filters Fast was made aware of a possible data security incident affecting its e-commerce website”. The company did not take their website offline to investigate, and therefore unaware customers were able to continue to shop on the compromised website. This means that any customer who purchased from the website between July 2019 and July 2020 most likely had their personal and credit card information stolen. The code was removed from the website on July 10th, 2020. Filters Fast notified customers between 14th-18th August 2020, one month after discovering the malicious code and patching the vulnerability. In a series of notification letters to various Attorney Generals, Filters Fast stated approximately how many individuals were affected in this data breach, and at the very least there were 30,000 victims in this attack.
American Payroll Association
On August 31st, Bleeping Computer reported a data breach on the American Payroll Association (APA), affecting members and customers. The attack was discovered on July 13th, 2020. The attackers used a security vulnerability in the content management system (CMS) to successfully inject a web-skimmer on the organisation’s login and online store checkout pages. According to APA’s Notice of Security Incident, the malicious activity was traced back to two months ago on May 13th. It is not known how many customers were affected, however, the APA has more than 20,000 members.

Warner Music Group
Warner Music Group (WMG) the third-largest global music recording company revealed they had suffered a data breach after a Magecart-style attack. The attack affects multiple US website stores which they operate via an external service provider. In a Notice of Data Breach, the company explains: “On August 5, 2020, we learned that an unauthorized third party had compromised a number of US-based e-commerce websites WMG operates but that are hosted and supported by an external service provider.” The websites were compromised for over four months between April 25th – August 5th, 2020. WMG explains that all information entered by those affected in the compromised stores was potentially harvested by the attackers.

FabFitFun
In a Notice of Data Breach, it was revealed that the FabFitFun U.S. website had been infected with malicious code, not once, but twice in a four-month timeline. FabFitFun informed customers that they had discovered “that an unauthorized third party inserted malicious code” on portions of their website. In their forensic investigation, it was revealed that the incident concerns the new member sign-up pages of the FabFitFun website. The site was compromised between April 26th and May 14th, 2020, and then again from May 22nd, and August 3rd, 2020. FabFitFun have removed the malicious code from their website, and have taken steps to secure their site.
Boom! Mobile
Boom! Mobile, a US-based mobile virtual network operator suffered a data breach due to a web-skimming attack on its website, conducted by the notorious cybercriminal Fullz House group. The site was compromised from September 30th, 2020 until 5th October 5th, 2020. The attack affected the shopping cart page on boom[.]us. According to Malwarebytes, Fullz House injected a single line of code, which contains a Base64 encoded URL loading an external JavaScript library. The URL is disguised as a Google Analytics script from paypal-debit[.]com/cdn/ga.js.

Wisepay
On October 7th, it was reported that Wisepay, a service that enables customers to pay for school meals and other school-related costs, had their website compromised. In a School & Parent Notice, parents at affected schools were told “At some point around 2 October 2020, we understand that a cyberattack occurred in the form of a URL manipulation, meaning that the payment gateway page was redirected or controlled by a bad actor, and your payment card data may have been unlawfully disclosed.” The compromise affected the website between October 2nd, 2020, and October 5th, 2020. A Wisepay spokesman explained that the attackers were “spoofing the Sagepay page to capture card details”. It is believed the compromise affected approximately 300 schools. The website was put into maintenance mode from Monday morning to fix the issue.
PlayBack Now
Bank Info Security reported that Video conference firm PlayBack Now was compromised in a web-skimming attack aiming to steal customer’s payment and personal data. The attackers created a typosquatting-based website and injected a web-skimmer into the Magento ecommerce platform within the websites PlayBack Now built for its customers. Approximately 40 PlayBack Now customers have been affected by the attack including the National Association of Realtors, American Diabetes Association, and the American College of Physicians. The number of end-customers who have been affected as a result of these compromised sites is unknown.
JM Bullion
On November 1st, it was reported that one of the largest sellers of precious metals in the world – JM Bullion, had suffered a web-skimming attack. The company was alerted to “suspicious activity” on July 6th, where they began an investigation using a third-party forensics team. The investigation showed that the malicious code had been present on the website from February 18, 2020, for 5 months until July 17th, 2020, when it was removed. The company says the malicious code could capture customer information in “limited scenarios” which form a small portion of the transactions processed on the site. It took JM Bullion over 3 months to inform their customers, which they did so on November 1st, 2020. This is an usually long delay for a data breach.
Jerry’s Music
The last Magecart attack reported in 2020 was on December 29th. Jerry’s Music is a musical instruments retailer located in Wisconsin and established in 1958. Félix Aimé reported the attack on Jerry’s Music, he tweeted: “#MageCart #JSSkimmer (yes, its been a while) at https://jerrysmusic[.]com/js/varien/validation.js.” The domain is a known malicious domain and linked to other skimmer domains. Had the retailer had Attack Detection this would have been flagged potentially before a data breach occurred. Little information is known about this attack, however, further research into Jerry’s Music shows a history of similar attacks. Max Kerstern also mentions Jerry’s Music in the report ‘Backtracking MageCart Infections’ published 6th May 2020. Jerry’s Music is among other retailers with malicious code found on its site. The first detection was on 20th October 2018 and the last detection on 16th August 2019. It is unknown whether this attack is still active and how many customers have been affected.
RapidSpike recommends companies to take responsibility for protecting customers’ data by having a multi-layered approach to security, including continuous monitoring to prevent and detect attacks.
RapidSpike security researchers have taken the time to investigate the client-side security attacks mentioned in the 2020 Magecart Timeline. We can confidently say our Attack Detection would have detected these types of attacks. Attack detection takes less than 5 minutes to set-up and will alert you to any untrusted data on your ecommerce site.







