Our sources state that there has been a 20% increase in web-skimming attacks since the outbreak of the COVID-19 virus. Recently, we have witnessed some high-profile Magecart attacks. The latest Magecart attacks include; American Payroll Association, music giant – Warner Music Group, and lifestyle subscription brand – FabFitFun.
American Payroll Association
At the start of the month, it was revealed that the American Payroll Association (APA) had suffered a data breach affecting members and customers. According to Bloomberg, the APA “operates as a non-profit organization. The Organization advocates for the payroll industry and payroll profession. APA provides social networking, membership services, government relations, educational resources, and courses and conferences.”
The attack was discovered on July 13th 2020. The attackers used a security vulnerability in the content management system (CMS) to successfully inject a web-skimmer on the organisation’s login and online store checkout pages. According to APA’s Notice of Security Incident, the malicious activity was traced back to two months ago on May 13th. In addition to stolen credit card information, other personal information which may have been stolen includes:
- First and last names
- Email address
- Job title and job role
- Primary job function and direct supervisor
- Gender
- Date of birth
- Address (either business of personal), including country, province or state, city, and postal code
- Company name and size
- Employee industry
- Payroll software used at workplace
- Time and attendance software used at work
- Profile photos and social media username information (for “some” accounts only)

It is not yet known how many customers were affected, however, the APA has more than 20,000 members. After the attack, APA’s security team increased the frequency of security patches and deployed anti-malware solutions on the affected servers. They are also offering identity theft insurance and free credit monitoring for affected customers.
Warner Music Group
Warner Music Group (WMG) the third-largest global music recording company revealed they had suffered a data breach after a Magecart-style attack.
The attack affects multiple US website stores which they operate via an external service provider. In a Notice of Data Breach, the company explains: “On August 5, 2020, we learned that an unauthorized third party had compromised a number of US-based e-commerce websites WMG operates but that are hosted and supported by an external service provider.”
The websites were compromised for over four months between April 25th – August 5th, 2020.
WMG explains that all information entered by those affected in the compromised stores was potentially harvested by the attackers. Stolen information includes: names, email addresses, telephone numbers, billing and shipping addresses, and payment card information. Those who made payments via PayPal were not affected.
A Warner Music Group spokesperson told BleepingComputer “E-commerce websites operated by Warner Music Group through a third-party e-commerce platform were targets of a cybersecurity attack, which potentially exposed credit card and related data that customers entered into the sites.” Going on to say “We are putting in place additional measures to prevent future breaches.” The WMG spokesperson declined to name the affected websites.
WMG launched a forensic investigation with an external cybersecurity firm, notified relevant card providers and law enforcement. WMG are offering free identity monitoring for those affected.
FabFitFun
In a Notice of Data Breach, it was revealed that the FabFitFun U.S. website had been infected with malicious code, not once, but twice in the last four months. FabFitFun is a lifestyle subscription box, providing beauty, home, and wellness and fitness items.
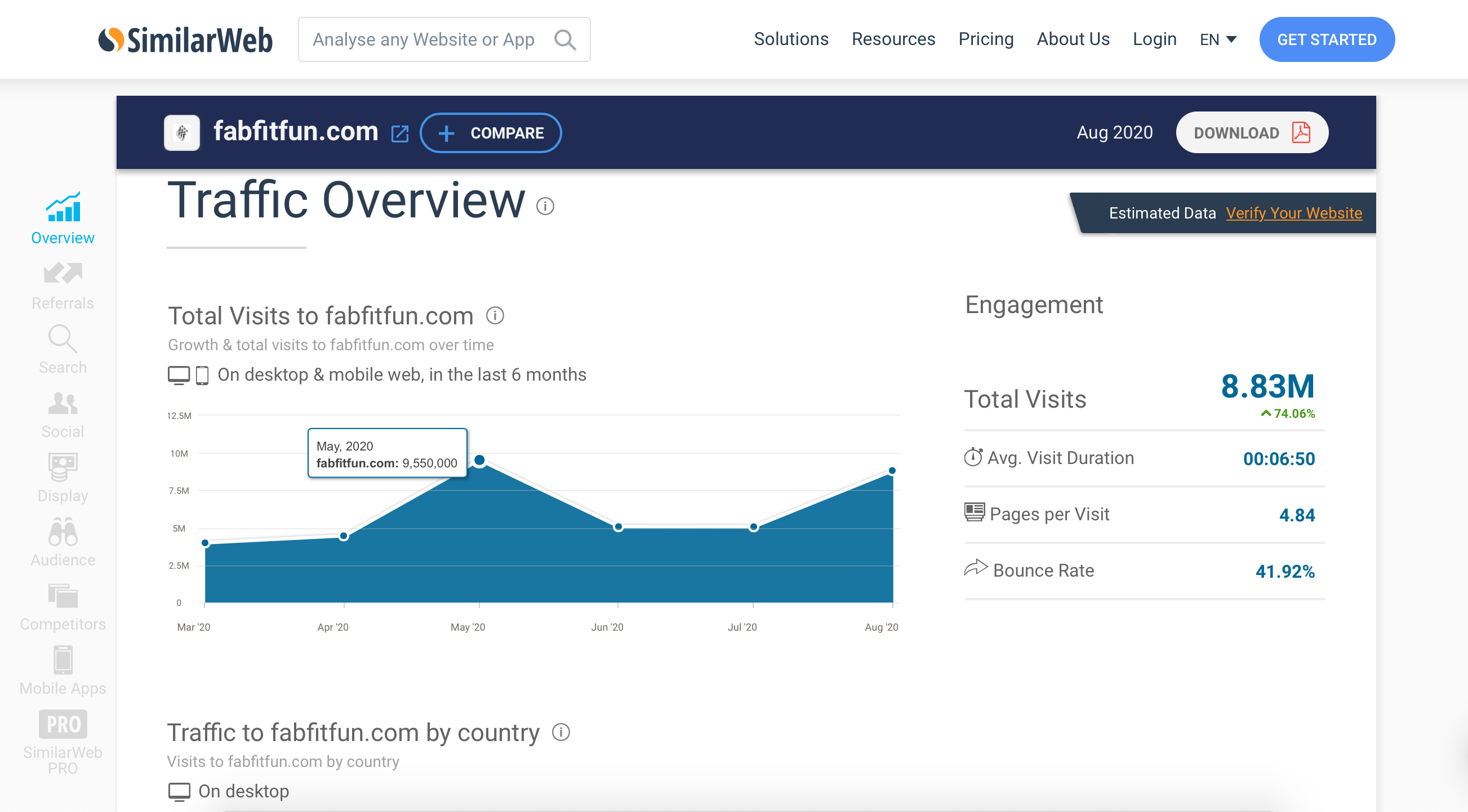
FabFitFun informed customers that they had discovered “that an unauthorized third party inserted malicious code” on portions of their website. In their forensic investigation, it was revealed that the incident concerns the new member sign-up pages of the FabFitFun website. The site was compromised between April 26th and May 14th, 2020 and then again from May 22nd, and August 3rd, 2020. According to SimilarWeb, FabFitFun had over 9.5 million website visitors in May, and over 5 million in both June and July, the total site visitors for the compromised period is approximately 20m.
The malicious code affected customers using different types of payment methods, not just credit cards. Stolen information included emails and passwords for customers that signed up using Paypal or Apple Pay, and name, address, and card information for other customers.
FabFitFun have now removed the malicious code from their website, and have taken steps to secure their site. They have offered identity protection services for customers, as well as offering $25 store credit to be used by the end of the year.
For obvious reasons, customers are not happy, with some reporting on social media that they have already had fraudulent activity on their card. A Reddit post with more than 107 comments, highlights the frustrations customers are facing:
“Someone stole my credit card number and charged more than $500 over this past weekend.”
“Luckily for me, Warner Music already leaked all my credit card data a month ago and people bought hundreds of dollars worth of clothes online.”
“I signed up at the beginning of June and within a week or two I had a fraud alert from my bank. They asked me if I had just used my card for almost $500 – I said no and they froze my card immediately. I’m on disability – had those charges gone through, I would have been screwed. I was super lucky but had I not been, a $25 voucher for a specific sale would not have made things right.”
RapidSpike security researchers have taken the time to investigate the client-side security attacks mentioned. We can confidently say our Attack Detection would have detected these types of attacks. Attack detection takes less than 5 minutes to set-up and will alert you to any untrusted data on your ecommerce site.






