Continuing our focus on Security Monitoring, in addition to our Data Breach Monitor feature we have released the latest addition to the toolset, Malicious User Detection.
What is Malicious User Detection?
The RapidSpike Malicious User Detection provides a way to be alerted when there is an increase of malicious users accessing your website or web application.
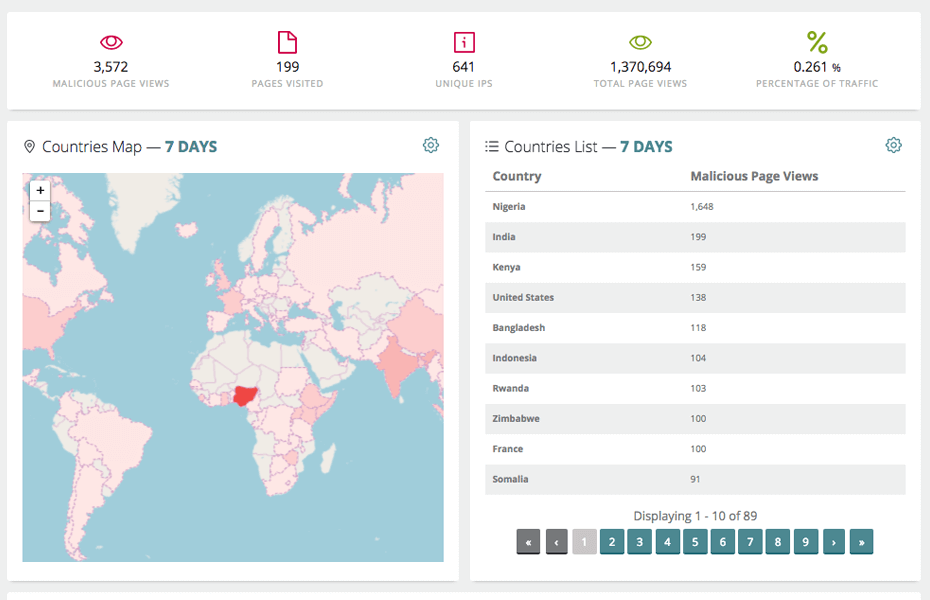
Information about the malicious users is presented in the user interface, including information broken down by country, pages visited and also a percentage of total traffic that is classed as malicious.
One key takeaway from the system is a downloadable network list that is available so that you can take this list and import it into your shun list on your perimeter firewall or other security device to prevent attackers from accessing your resources.
This is particularly useful when your website is under a botnet or other type of automated attack such as a DDoS attack as you can identify the exact source of the traffic and be provided with a network shun list to prevent the attackers from accessing your resources.
If you configure the system to alert you as an attack is increasing, this can act as an early warning system that provides you with an indication of an impending situation and allows you to take action before a failure would occur.
How does Malicious User Detection work?
The RapidSpike Malicious User Detection system harnesses the power of Real User Monitoring (RUM) technology to identify when your website or web application is being targeted by known malicious users and networks.
Once RUM is configured by adding the required JavaScript code, RapidSpike is able to track the source of every client that accesses your website or web application in real time.
All traffic to your website or web application is compared to our Malicious User List and any matches are identified in real time. These matches can alert you to when your website is being targeted by botnets, attack networks and rogue proxy servers amongst others enabling you to take action.
The Malicious User List protects against threats arising from cyber-crime related networks such as unroutable IPs, Bogon networks, known attacking networks, known botnet networks, known malware networks, known DDoS command and control networks and rogue proxy networks.
The Malicious User List is a proprietary IP based list that has been created by our team of security researchers. The list contains several hundred million malicious IP addresses and is constantly updated with IP addresses added and removed as required. The list is made up of a best practice collection of networks that have been identified as malicious and are considered safe to block from accessing your resources.
How to setup Malicious User Detection
The first step to configuring Malicious User Detection is to ensure that Real User Monitoring is configured and working on your website or web application. If you try to browse to the Malicious User Detection configuration menu without RUM being enabled you will receive notification that RUM is not enabled:
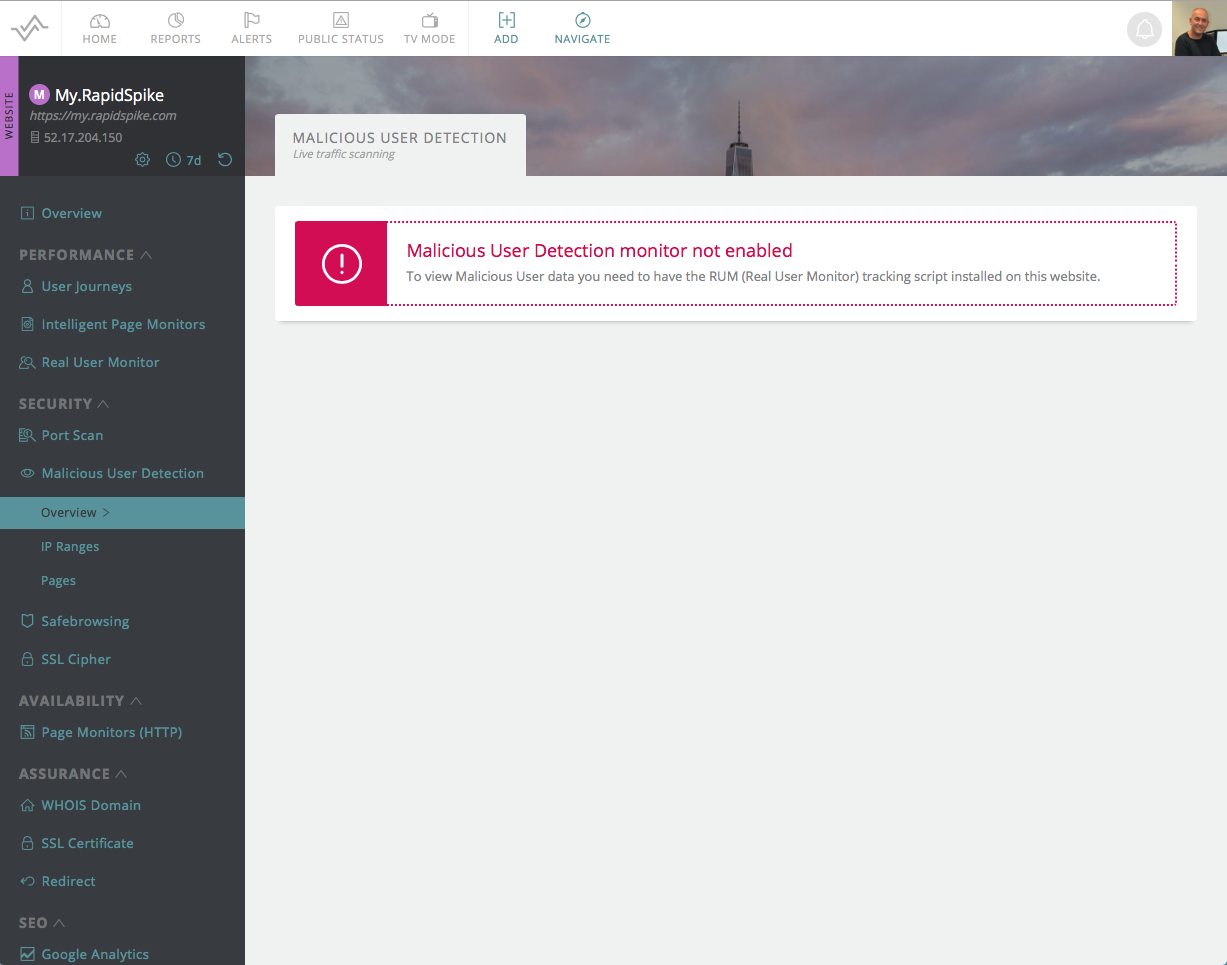
If RUM is configured for your website, and you have the appropriate license, then Malicious User Detection will be enabled by default. There are no additional steps to enable the comparison against the Malicious User List.
Receiving Malicious User Detection Alerts
In its default enabled state, Malicious User Detection will compare all website traffic against the Malicious User List and it will provide you with the information within the user interface of any matches along with a network blocklist that you can download as a CSV file to enable blocking on a perimeter device.
You can configure Alerts to notify you by the method of your choice when you are receiving an increase in malicious traffic.
To enable the alert, navigate to the Alerts menu item and select Malicious User Detection Rules to configure the rule you require.